Troubleshooting Defender for Endpoint connectivity issues
31 December 2023
Troubleshooting Defender for Endpoint connectivity issues
In this post I want to show you which requirements you need to fulfil to successfully use Defender for Endpoint on your managed devices within your network.
Which network requirements are there?
At the time of the writing of this post the following backend endpoints needs to be accessibly from your devices:
| Service Description | URL |
|---|---|
| Microsoft Defender Antivirus cloud-delivered protection service (referred to as Microsoft Active Protection Service - MAPS) | *.wdcp.microsoft.com, *.wdcpalt.microsoft.com, *.wd.microsoft.com |
| Microsoft Update Service (MU) and Windows Update Service (WU) | *.update.microsoft.com, *.delivery.mp.microsoft.com, *.windowsupdate.com, ctldl.windowsupdate.com |
| Security intelligence updates Alternate Download Location (ADL) (Alternate location for Microsoft Defender Antivirus Security intelligence updates if out of date) | *.download.microsoft.com, *.download.windowsupdate.com (Port 80), go.microsoft.com (Port 80), https://www.microsoft.com/security/encyclopedia/adlpackages.aspx, https://definitionupdates.microsoft.com/download/DefinitionUpdates/, https://fe3cr.delivery.mp.microsoft.com/ClientWebService/client.asmx |
| Malware submission storage (Upload location for files submitted via Submission form or automatic sample submission) | ussus1eastprod.blob.core.windows.net, ussus2eastprod.blob.core.windows.net, ussus3eastprod.blob.core.windows.net, ussus4eastprod.blob.core.windows.net, wsus1eastprod.blob.core.windows.net, wsus2eastprod.blob.core.windows.net, ussus1westprod.blob.core.windows.net, ussus2westprod.blob.core.windows.net, ussus3westprod.blob.core.windows.net, ussus4westprod.blob.core.windows.net, wsus1westprod.blob.core.windows.net, wsus2westprod.blob.core.windows.net, usseu1northprod.blob.core.windows.net, wseu1northprod.blob.core.windows.net, usseu1westprod.blob.core.windows.net, wseu1westprod.blob.core.windows.net, ussuk1southprod.blob.core.windows.net, wsuk1southprod.blob.core.windows.net, ussuk1westprod.blob.core.windows.net, wsuk1westprod.blob.core.windows.net |
| Certificate Revocation List (CRL) (Used for SSL connection to MAPS for updating CRL) | http://www.microsoft.com/pkiops/crl/, http://www.microsoft.com/pkiops/certs, http://crl.microsoft.com/pki/crl/products, http://www.microsoft.com/pki/certs |
| Universal GDPR Client (Used for sending client diagnostic data for product quality and monitoring purposes) | TCP Port 443 at: vortex-win.data.microsoft.com, settings-win.data.microsoft.com |
To get the latest information check out the „Services and URLs“ section in Microsoft Learn.
How to validate cloud-delivered protection?
The cloud delivery protection helps your device by using compute power from the Cloud for your device security. So it is important that this feature works without issues. You can check if the connection to MAPS works by using the MpCmdRun app from Defender for Endpoint right on your devices:
"%ProgramFiles%\Windows Defender\MpCmdRun.exe" -ValidateMapsConnection
How to validate SmartScreen protection?
Defender SmartScreen helps by blocking unwanted or dangerous files. You maybe know this feature when you ever had a complete red window in your Edge browser which told you that a site or download has been blocked. This could look like this:
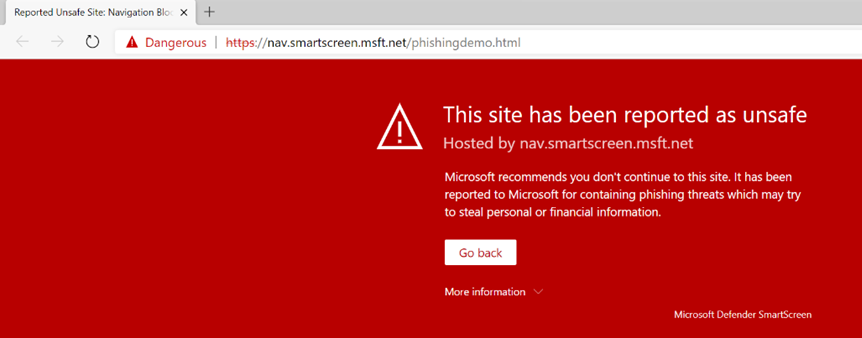
To test if SmartScreen is running and working, simply navigate to https://aka.ms/ioavtest1, this will trigger a warning.
Using Microsoft Defender for Endpoint client analyzer
But one of the coolest tip in my opinion is to use the client analyzer from Defender for Endpoint. This tool can be run right from a console once you have downloaded it and it will check if all network endpoints from the backbone are reachable and if everything is configured so that Defender for Endpoint can work without issues.
You can download the tool from Microsoft Learn. It is available for Windows, macOS and Linux.
Let me show you how it works on Windows.
First I am going to download the tool on my machine:
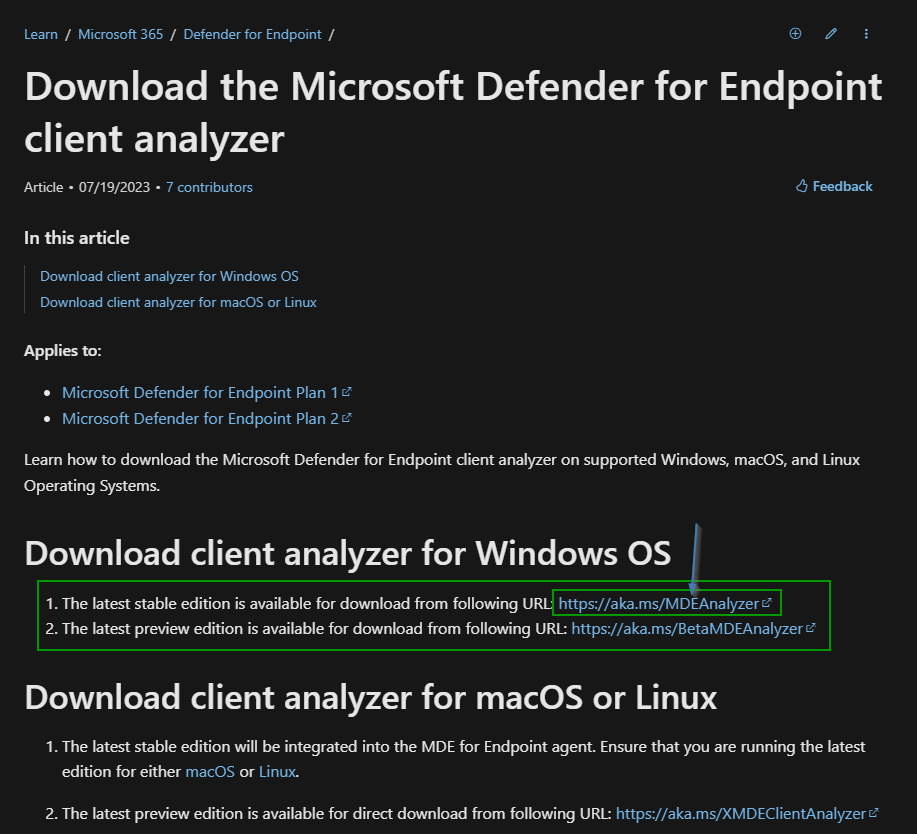
Once downloaded unzip the file, open a PowerShell/CMD as Administrator and navigate to the extracted tool folder and execute „.\MDEClientAnalyzer.cmd“:
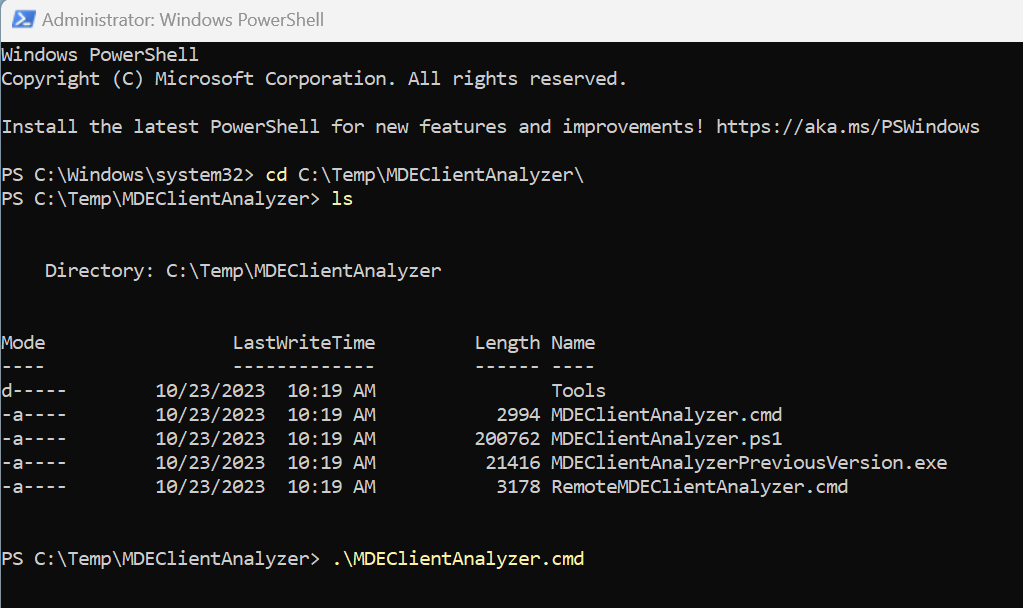
This will write some output on the console but let the script finish to get a website which tells you everything:
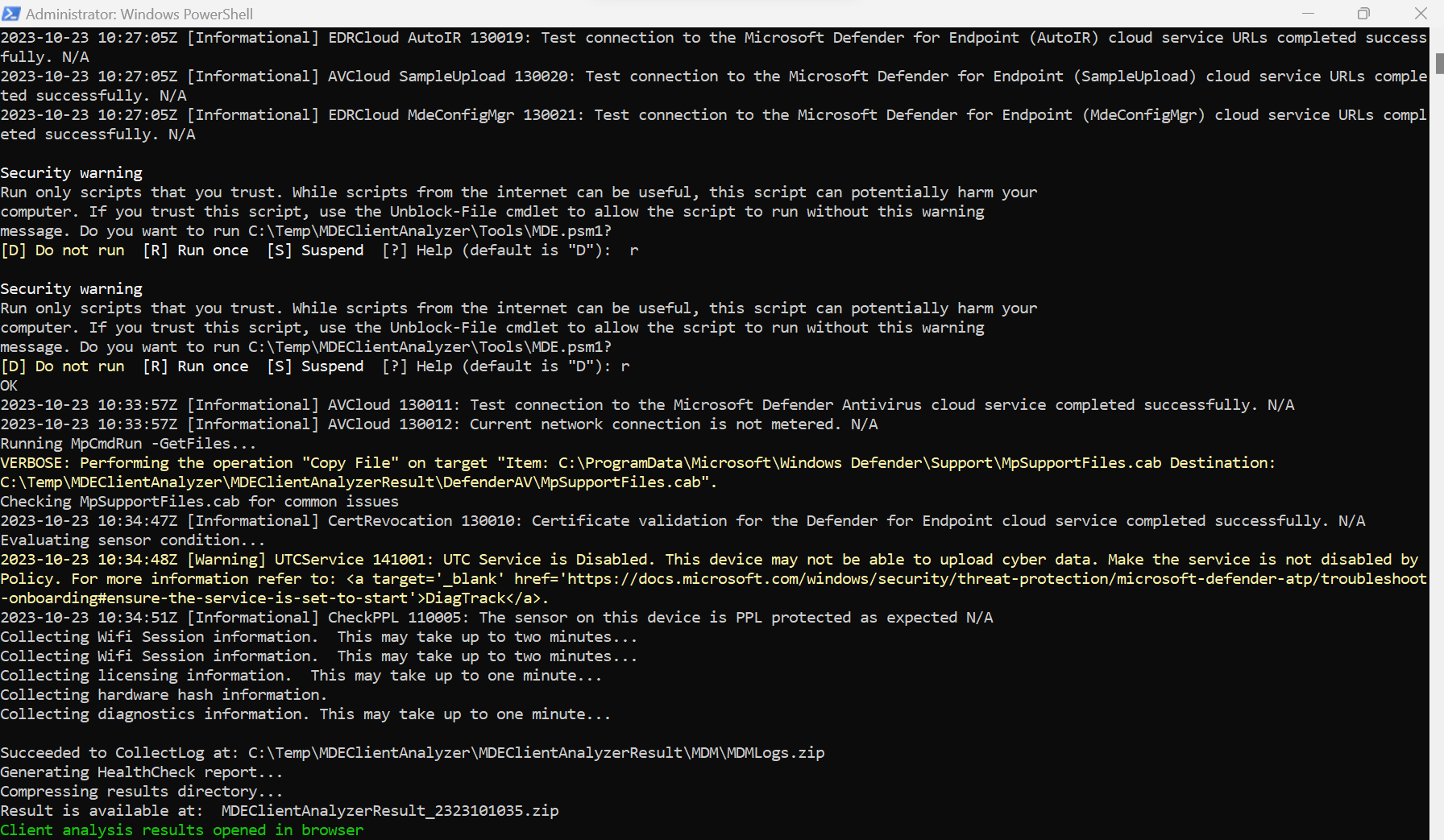
One the script finishes it will automatically open the create status website:
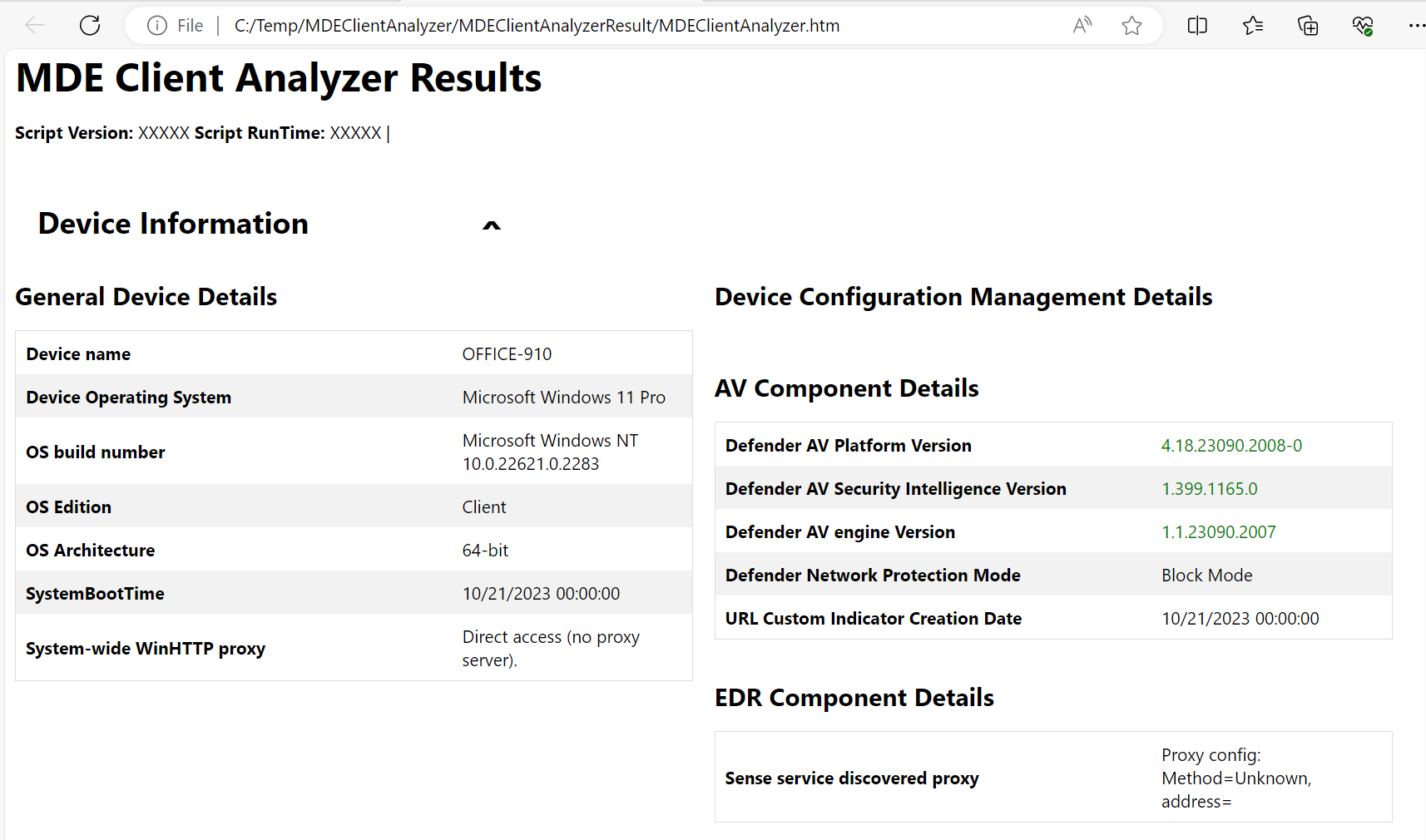
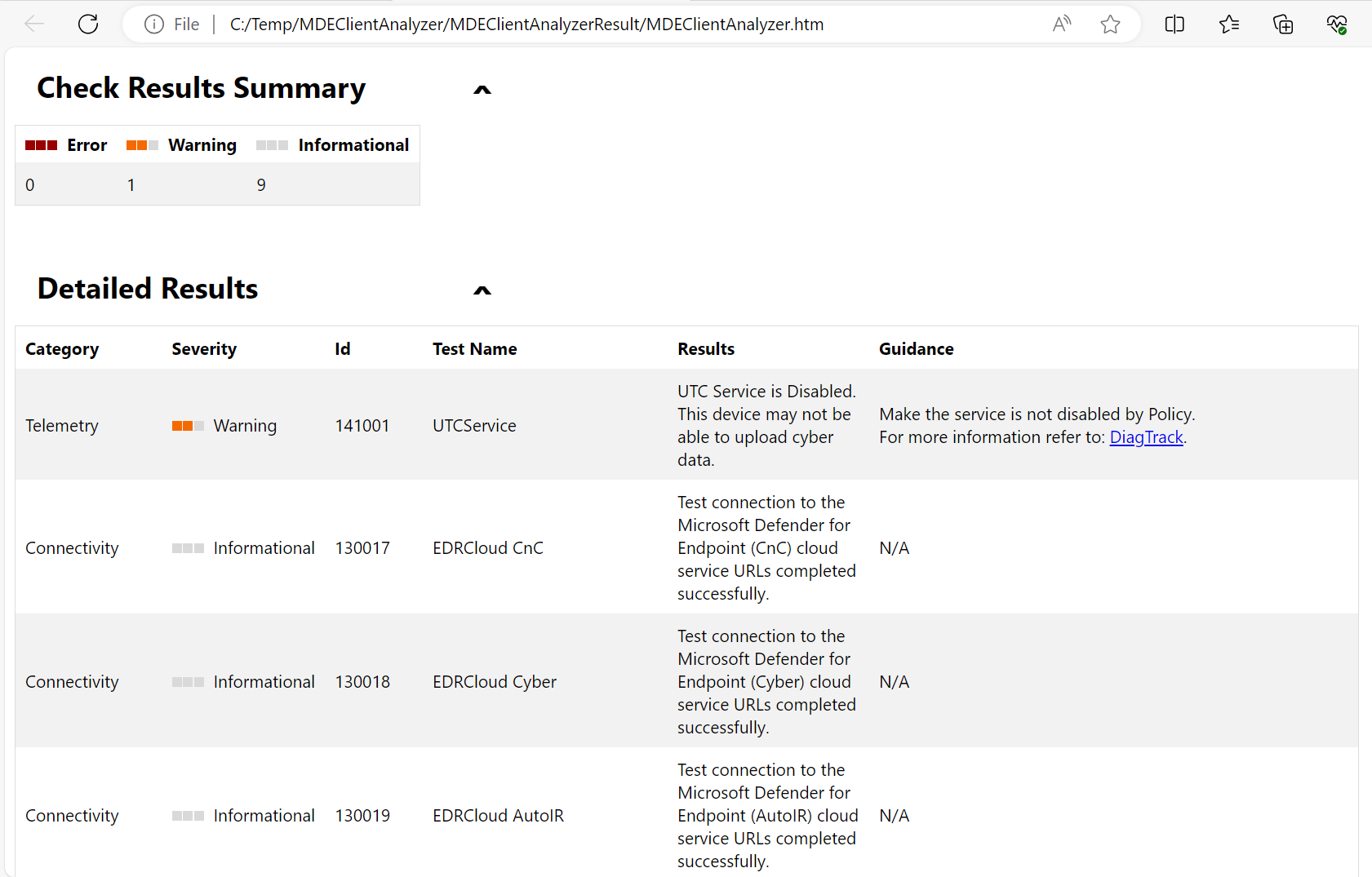
Here you find the status in the top page and if you scroll down you will find detailed results and issues:
RSS Update feed
If you want to can add the Microsoft Learn page on the network requirements for Defender for Endpoint to your RSS feed by using the URL https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/security/defender-endpoint/configure-network-connections-microsoft-defender-antivirus.md.atom. This allows you to get updates right in your inbox.
Conclusion
Those tools and specially the MDEClientAnalyzer are very easy to use and help you to identify problems with your Defender for Endpoint setup. If you ever have issues simply use those tips to get the issue and fix it.
I would recommend you to try the tool and learn how it work and how you need to analyze it so that if you need it one day you already know where you get help and how you can use it.