Configuring Windows Firewall Profile to Domain when connected to corporate SSID on an Entra ID joined and Intune managed device.
31 December 2023
Configuring Windows Firewall Profile to Domain when connected to corporate SSID on an Entra ID joined and Intune managed device.
In today’s digitally connected world, ensuring the security of corporate networks is paramount. With the rise of remote work and the increasing complexity of cyber threats, organizations need robust solutions to protect their data and infrastructure. One crucial aspect of this protection is configuring firewalls effectively, particularly on Windows devices connected to corporate networks.
Microsoft Intune, a cloud-based service that enables device management and security, offers a powerful feature for configuring Windows Firewall profiles when connected to corporate SSIDs. This feature, known as „Network List Manager,“ allows administrators to define specific criteria for activating the Domain Firewall profile based on network conditions.
In this blog post, we will explore how to leverage Network List Manager in Microsoft Intune to configure Windows Firewall profiles dynamically.
Configuring a trusted network
By specifying the corporate wireless SSID and defining allowed TLS authentication endpoints, administrators can ensure that devices activate the Domain Firewall profile only when connected to trusted networks and accessing authorized resources. Once that is active you can configure Windows Firewall rules that only apply then your devices are connected within the corporate network. Now that we all are remote working you also could define your VPN adapter as the SSID name so the profile activation rule will apply on a VPN connection.
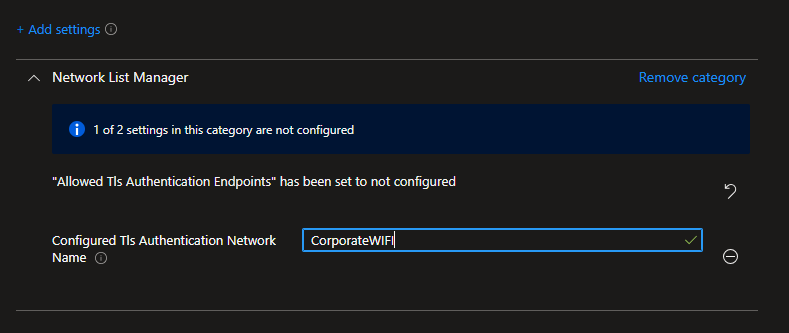
Lets start by configuring „Configured Tls Authentication Network Name“ which will define our trusted network.
Go to the Intune portal and create a new settings catalog profile. Define a name and an description, then firstly search for „Configured Tls Authentication Network Name“:
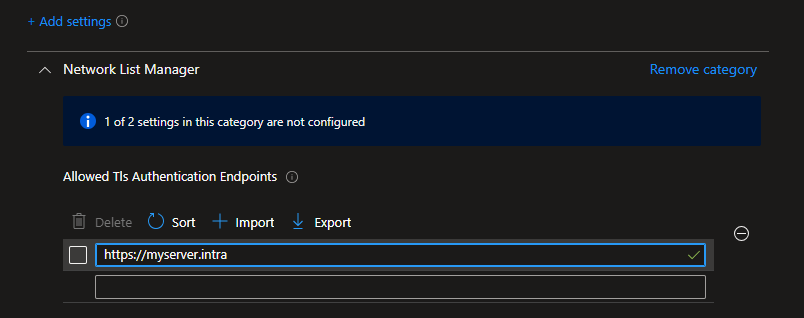
Next search for „Allowed Tls Authentication Endpoints“ and define an HTTPS url that is only reachable within your network and will return a HTTP code of 200:
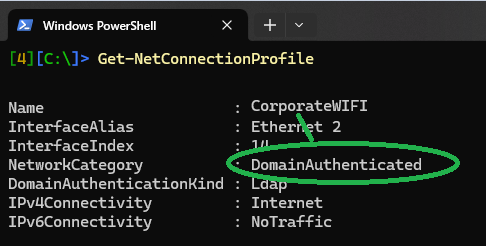
You can test if the profile is applied by checking the Windows Firewall and review the profile or by using the PowerShell command „Get-NetConnectionProfile“:
Conclusion
In conclusion, configuring Windows Firewall profiles to activate the Domain profile when connected to corporate SSIDs using Microsoft Intune’s Network List Manager feature is a proactive step towards enhancing network security. By leveraging this capability, organizations can enforce stricter firewall policies on devices accessing corporate resources, thereby reducing the risk of unauthorized access and data breaches.
Through the careful configuration of the „Configured TLS Authentication Network Name“ and „Allowed TLS Authentication Endpoints,“ administrators can ensure that Windows devices activate the Domain Firewall profile only when connected to trusted networks and accessing approved resources. This granular control adds an extra layer of defense against potential threats, safeguarding sensitive data and maintaining regulatory compliance.