Enhancing Security with Windows Hello for Business Cloud Trust in Hybrid Environments
31 December 2023
Configuring Windows Hello for Business Cloud Trust
In the ever-evolving landscape of cybersecurity, organizations are constantly seeking robust solutions to ensure their data and systems remain protected. One such innovative tool that has gained prominence is Windows Hello for Business Cloud Trust. This technology offers a new level of authentication and security, particularly in hybrid scenarios where cloud-based and on-premises resources are integrated. In this blog post, we’ll dive into the intricacies of Windows Hello for Business Cloud Trust, the concept of Cloud Trust, its significance in hybrid environments, and the key differences between Cloud Trust and Key Trust.
Understanding Windows Hello for Business
Windows Hello for Business is a modern authentication platform developed by Microsoft that leverages biometric factors like fingerprint recognition, facial recognition, and PINs to provide users with a seamless, password-free experience. This approach enhances security by reducing the risks associated with password-based authentication, such as phishing and brute-force attacks. By utilizing biometric information, Windows Hello for Business offers a more secure and convenient way for users to access their devices and applications.
As you might ask where Windows Hello saves biometric data you need to know that those information’s are stored locally and secured on the device. It never leaves the device and also does not roam.
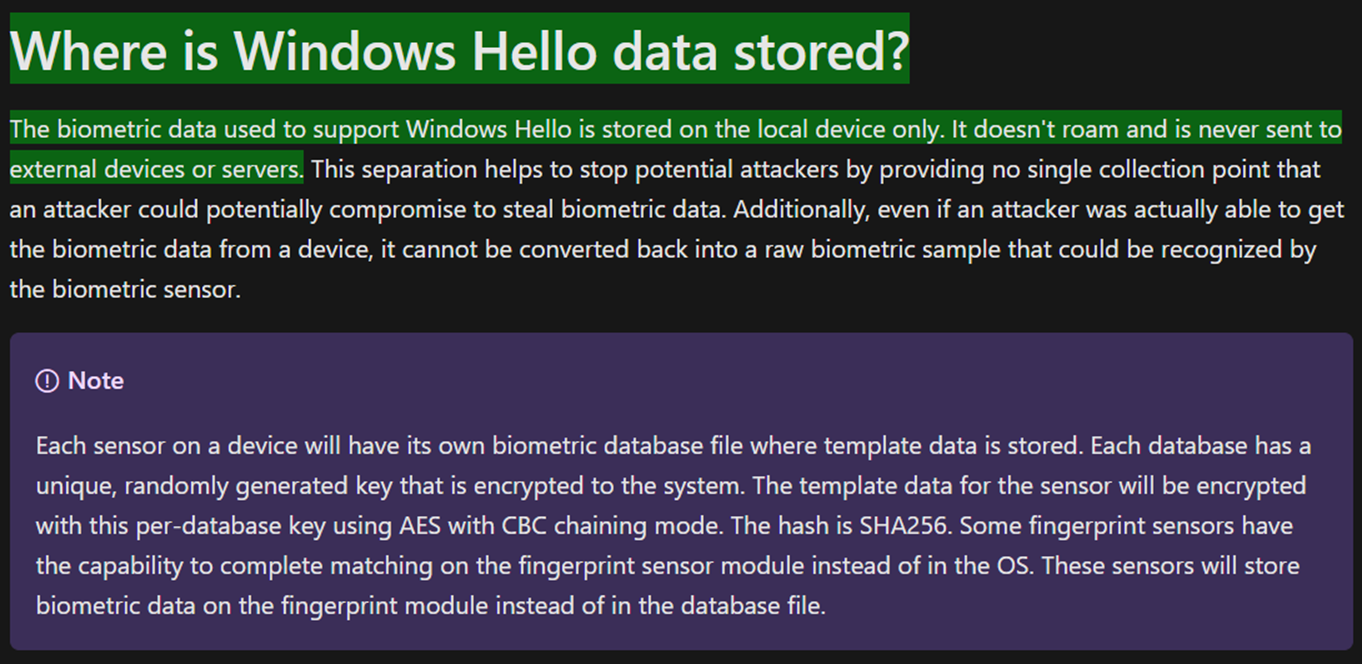
If you want to read more about the security you can check out this Microsoft Learn page HERE.
Introducing Cloud Trust
In the realm of cybersecurity, trust is paramount. Cloud Trust refers to the confidence that an organization places in cloud-based services to securely manage sensitive information. Cloud Trust involves a combination of security measures, compliance protocols, and data protection mechanisms to ensure the integrity and confidentiality of data stored and processed in the cloud. Windows Hello for Business Cloud Trust builds on this concept by integrating the trust established within cloud services with the modern authentication capabilities of Windows Hello. It enables you to use security features and modern authentication within an hybrid environment.
Lets see how the authentication works:
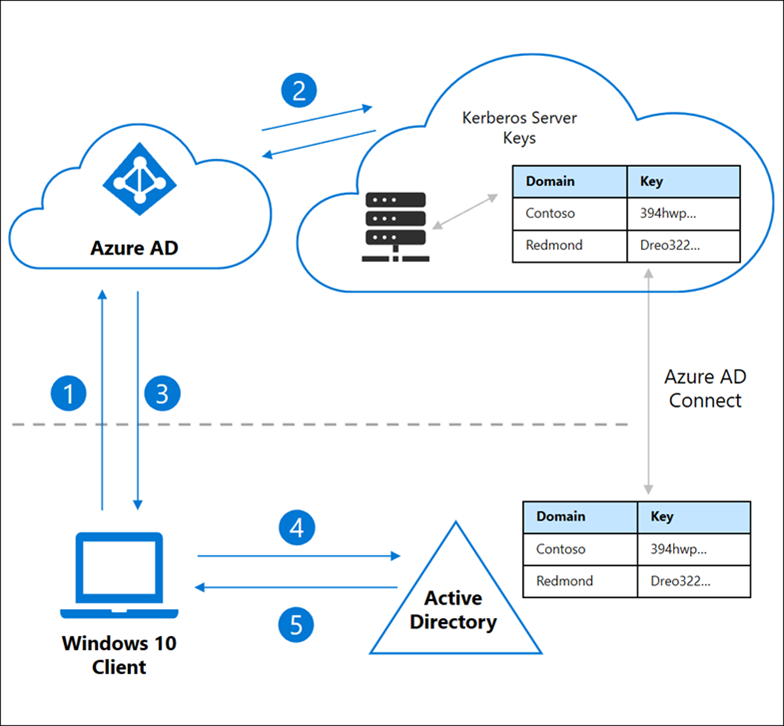
-User sign-in on the client with Windows Hello for Business based on modern Authentication by Azure AD.
- Azure AD checks for the Kerberos server key of the users UPN over Azure AD Connect in the local AD.
- Azure AD creates a Kerberos Ticket-Granting-Ticket (TGT) for the users UPN in the local AD. Within the TGT the SID of the users UPN is saved. Azure AD sends the TGT with it own Azure AD Primary Refresh Token (PRT) to the client.
- Now that the client has the TGT he can connect to the onprem domain controller to exchange its partial TGT to an full-formatted TGT for the Kerberos authentication.
- With the full-formatted TGT the Client now can easily access onprem resources over Kerberos and Cloud resources over modern Authentication from Azure AD.
Setup Windows Hello Cloud Trust
First of all you need to fulfil some requirements:
- You need an working onprem Active directory infrastructure, based at least on an functional domain level of Windows Server 2016.
- You need an working Azure AD with MFA configured
- You need an working Azure AD Connect V2, configured to sync identities and enabled Hybrid Azure AD join for your clients.
- Your Clients need to be at least Windows 10 21H2 or Windows 11 21H2.
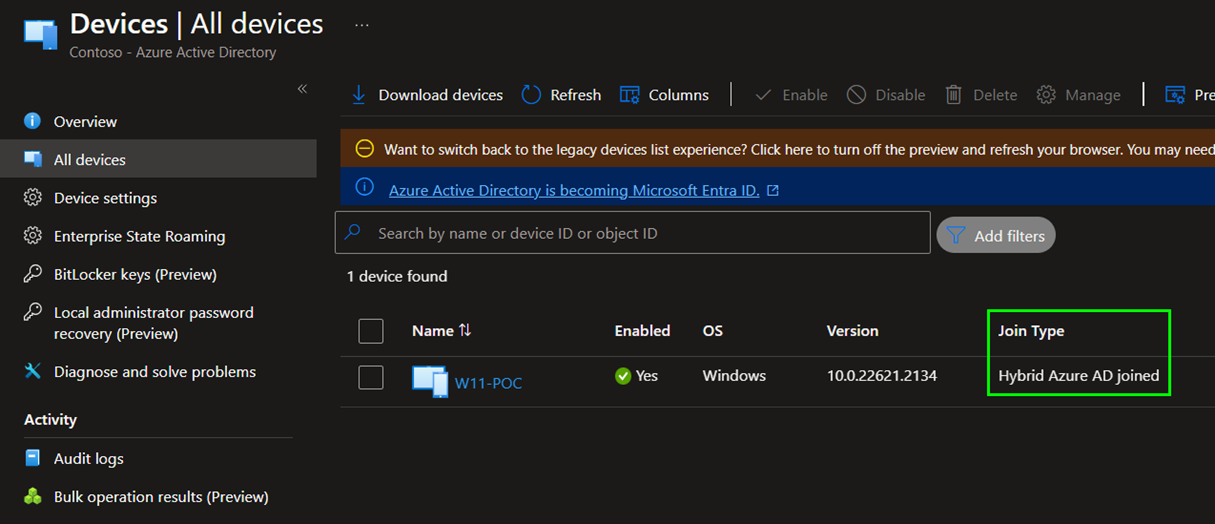
Check that you have your Clients in Azure AD, marked as „Hybrid Azure AD joined“:
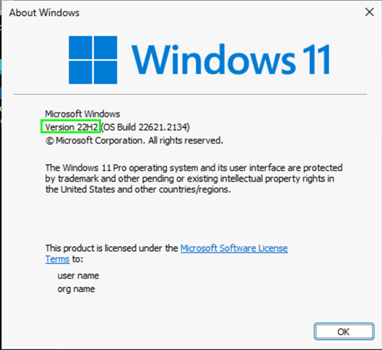
Check that your Windows clients are at least 21H2:
When you meet the requirements you can start with creating an Azure AD Kerberos Server object in your onprem Active directory. So you need to open an administrative PowerShell on your domain controller.
Next we are going to install the PowerShell module:
# Install the module
Install-Module -Name AzureADHybridAuthenticationManagement -AllowClobber
Now we create some variables. Please change „globaladmin@domain.onmicrosoft.com“ to an Global Administrator account from your Azure AD, this account will be used to create the Azure AD Kerberos Server connection, but it is not used for it to authenticate later. This will bring you an Authentication box where you need to enter the credentials of an domain admin user from your onprem AD:
```powershell
# Get your domain
$domain = $env:USERDNSDOMAIN
# Enter a domain administrator username and password.
$domainCred = Get-Credential
# UserPrincipalName of an Azure AD Global Administrator
$userPrincipalName = „globaladmin@domain.onmicrosoft.com"
Lastly we need to use a command from the module to create the Azure AD Kerberos Server object in our onprem AD. This will promt you with an Azure AD authentication popup where you need to authenticate with an Global Administrator from your Azure AD:
# Create the new Azure AD Kerberos Server object in Active Directory
Set-AzureADKerberosServer -Domain $domain -UserPrincipalName $userPrincipalName -DomainCredential $domainCred
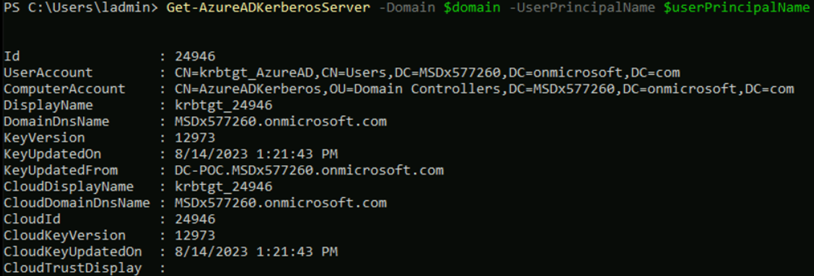
After you have authenticated here the object should be created in your onprem AD. To check you can either type
Get-AzureADKerberosServer -Domain $domain –UserPrincipalName $userPrincipalName
in your active PowerShell session an it will show you that there is an object created:
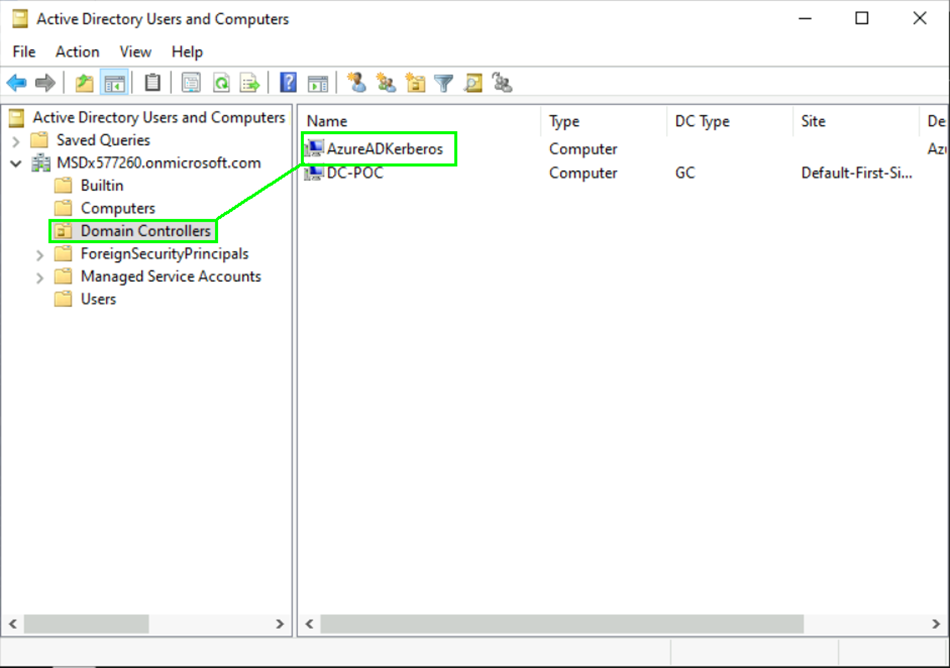
or you could also open the „Active Directory Users and Computers“ console and check under „Domain Controllers“ that the AzureADKerberos object is created:
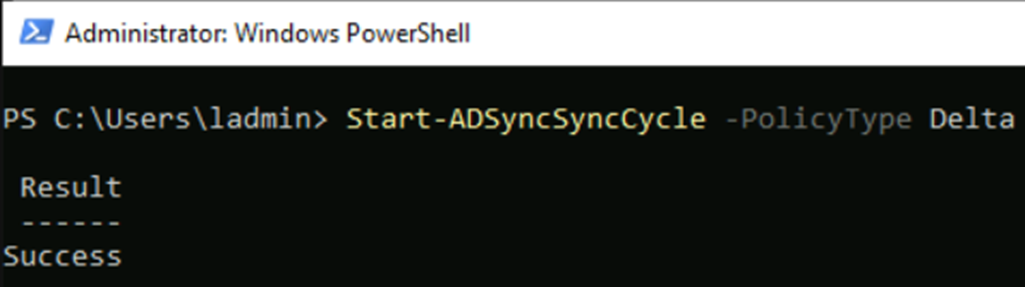
To finish the setup you should initiate an Azure AD Connect V2 sync cycle. You can do this from the server that hosts your Azure AD Connect from PowerShell with the following command:
Start-ADSyncSyncCycle -PolicyType Delta
Wait a few minutes, depending on the size of your onprem AD this can take a few minutes.
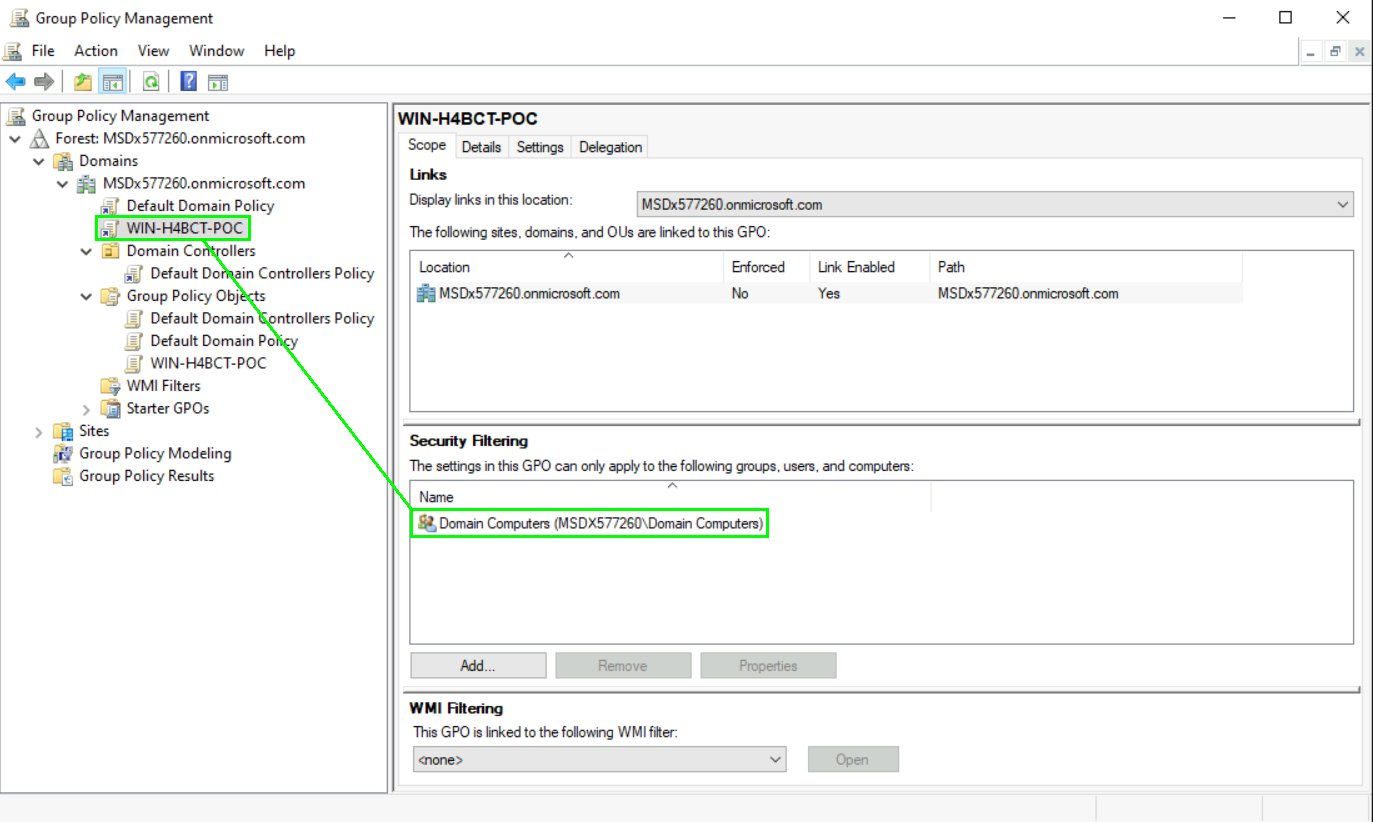
Configuring a Windows Hello for Business GPO
You also need to configure an GPO to enable Windows Hello for Business an your Windows clients. To do so you need to open the „Group Policy Management“ console within your onprem AD. Please create a new policy and set the Security Filtering on „Domain Computers“ and assign the policy to the organizational unit where your clients are located:
Next you need to configure Windows Hello for Business under „Computer Configuration -> Administrative Templates -> Windows Components -> Windows Hello for Business“. Enable the following settings:
- Use a hardware security device
- Use Windows Hello for Business
- Use cloud trust for on-premises authentication
Close the policy editor to save changes.
End-user Experience
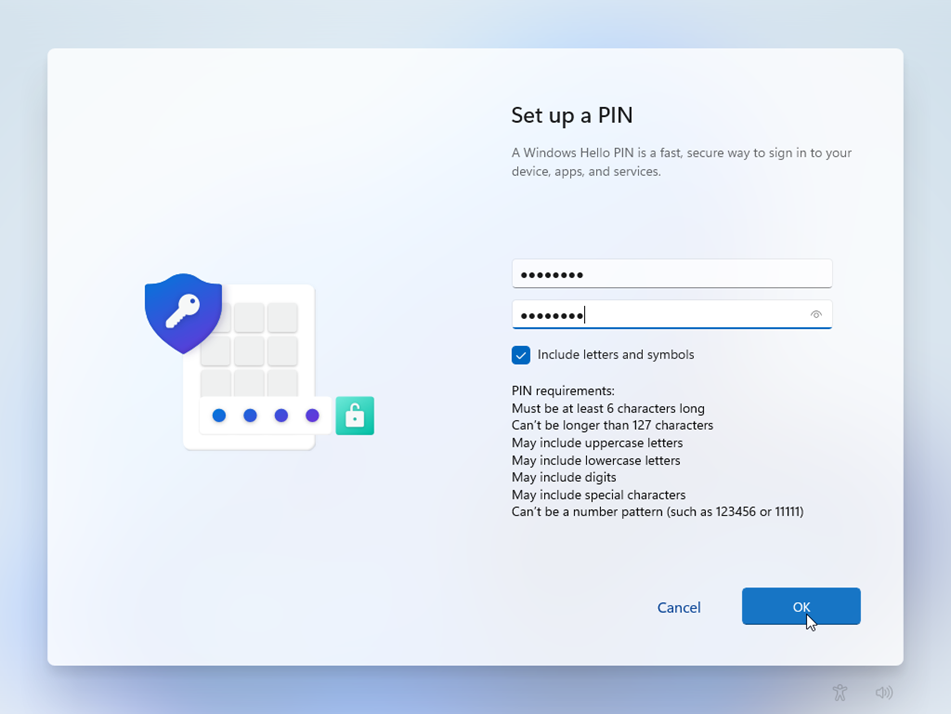
Once the policy has been applied to your Windows clients, the next time a user is signing in to Windows the user will be prompted to configure Windows Hello.
Depending on your client hardware the user can setup:
- Facial recognition
- Fingerprint recognition
- PIN
- Security Keys
Once configured the use can use the Windows Hello sign-in method at the next login. For example PIN:
The Significance in Hybrid Scenarios
Hybrid environments, where organizations operate a combination of on-premises infrastructure and cloud services, present unique security challenges. Windows Hello for Business Cloud Trust bridges the gap between these two domains by extending the security benefits of Windows Hello to both cloud-based and on-premises resources. This integration ensures consistent and secure authentication regardless of where the resources are located. As organizations increasingly adopt hybrid architectures, the need for a unified and strong authentication mechanism becomes critical to prevent potential security vulnerabilities.
Windows Hello for Business Cloud Trust and its Role in AD-AAD Integration for SSO and Kerberos
One of the most critical aspects of modern enterprise architecture is the seamless integration between on-premises Active Directory (AD) and Azure Active Directory (AAD) in hybrid environments. This integration is essential for achieving Single Sign-On (SSO) capabilities and maintaining a smooth user experience across both on-premises and cloud resources. Windows Hello for Business (Cloud Trust) plays a pivotal role in enhancing this integration, facilitating SSO and leveraging the power of Kerberos authentication for a secure and unified authentication experience.
Single Sign-On (SSO) and Windows Hello for Business Cloud Trust
Single Sign-On (SSO) is a user authentication process that enables users to access multiple applications and services with a single set of credentials. This streamlined experience enhances user productivity and minimizes the need for repeatedly entering usernames and passwords. Windows Hello for Business (Cloud Trust) enhances SSO capabilities by providing users with biometric-based authentication, enabling them to seamlessly access both on-premises and cloud-based resources without the need for traditional passwords.
When integrated with AAD, Windows Hello for Business (Cloud Trust) extends SSO across various devices and platforms. Users can log in to their devices using biometric authentication, and this authentication is then used to access AAD-protected resources in a secure and efficient manner. The cloud-based authentication process, based on biometric factors or PINs, further solidifies user identity, contributing to a higher level of trust in the authentication process.
Kerberos Authentication and Cloud Trust
Kerberos is a widely used network authentication protocol that provides strong authentication for client-server applications by using symmetric key cryptography. In a hybrid environment where both on-premises AD and cloud-based AAD coexist, maintaining consistent authentication mechanisms is vital. Windows Hello for Business (Cloud Trust) enhances this integration by acting as a bridge between traditional Kerberos-based authentication and modern biometric-based authentication.
When a user logs in to a device using Windows Hello for Business (Cloud Trust), the underlying authentication process involves both the device and the cloud. This process generates a token that can be used to access various resources, including those protected by Kerberos authentication. This token is trusted by both on-premises AD and cloud-based AAD, enabling the user to access resources across both environments without the need for multiple logins or complex authentication steps.
Benefits of Windows Hello for Business (Cloud Trust) in AD-AAD Integration
- Seamless Experience: Users can enjoy a consistent and seamless experience when accessing resources across on-premises and cloud environments, minimizing disruptions and boosting productivity.
- Enhanced Security: Windows Hello for Business (Cloud Trust) enhances security by utilizing biometric factors and eliminating the need for passwords, reducing the risk of phishing and credential-based attacks.
- Unified Identity: By bridging the gap between traditional AD and modern AAD, Windows Hello for Business (Cloud Trust) helps maintain a unified identity and authentication process.
- Efficient Management: Cloud-based authentication simplifies user management tasks, such as provisioning and deprovisioning, and offers scalability as the organization grows.
Cloud Trust vs. Key Trust
Cloud Trust and Key Trust are two authentication models within Windows Hello for Business, each with its own approach to securing user authentication.
- Cloud Trust: In Cloud Trust, the biometric or PIN data is sent to the cloud for verification. The cloud validates the user’s identity and returns a token that grants access. This model is suitable for scenarios where organizations are comfortable with sending biometric data to the cloud for verification, as it offers the benefits of seamless access and scalability.
- Key Trust: Key Trust, on the other hand, keeps the biometric or PIN data on the device itself. The verification process occurs locally, without sending data to the cloud. This model is ideal for scenarios where organizations have stricter data privacy concerns and want to ensure that biometric data never leaves the device.
Troubleshooting
In case that a devices does not enroll to Hybrid Azure AD joined you can try the command „dsregcmd /status“ to check it locally:
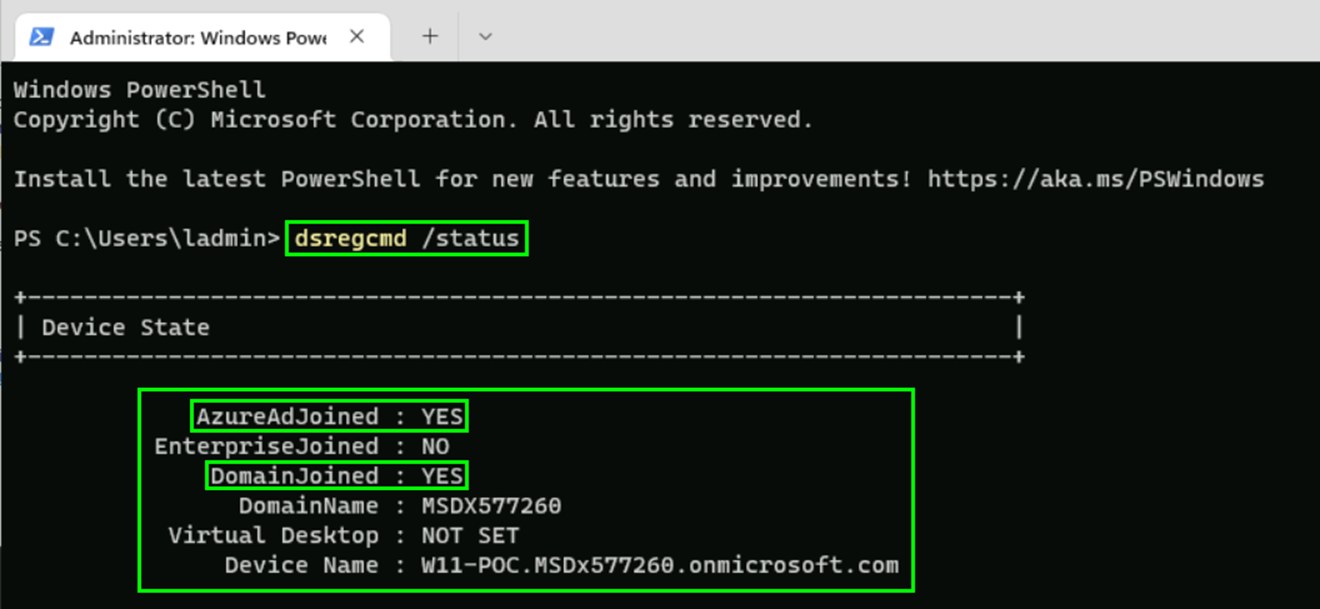
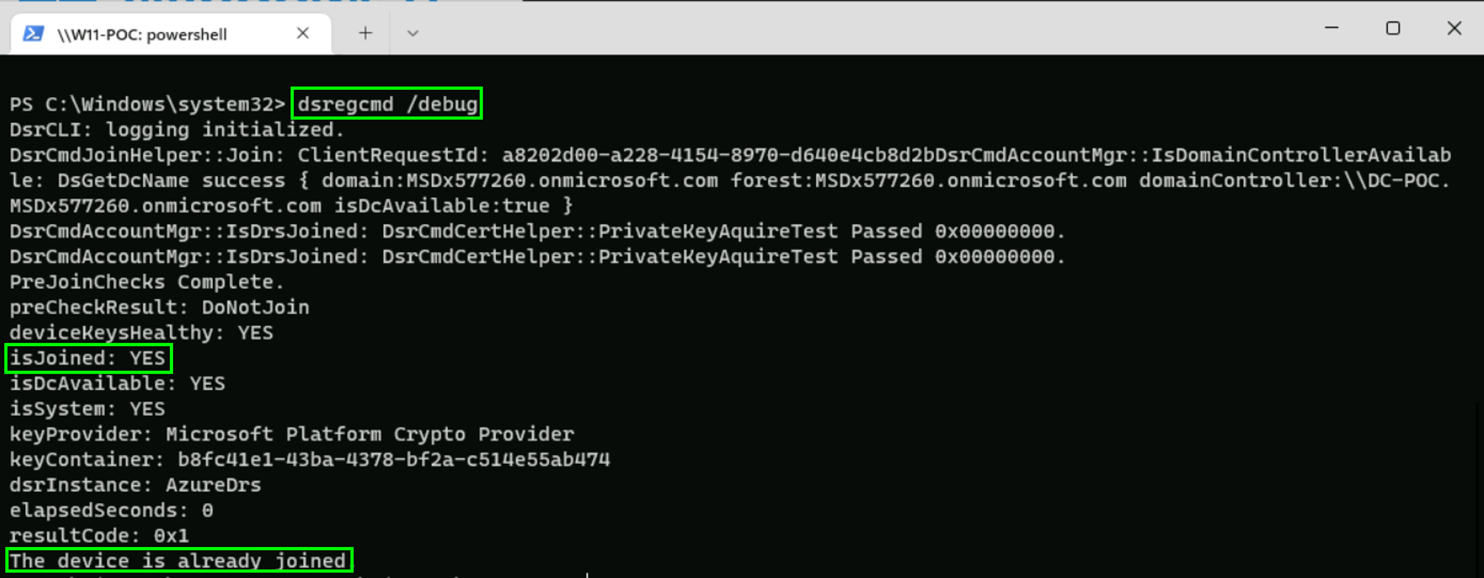
If your device is not showing „YES“ at „AzureAdJoined“ you might want to execute the command „dsregcmd /debug“ to get further details:
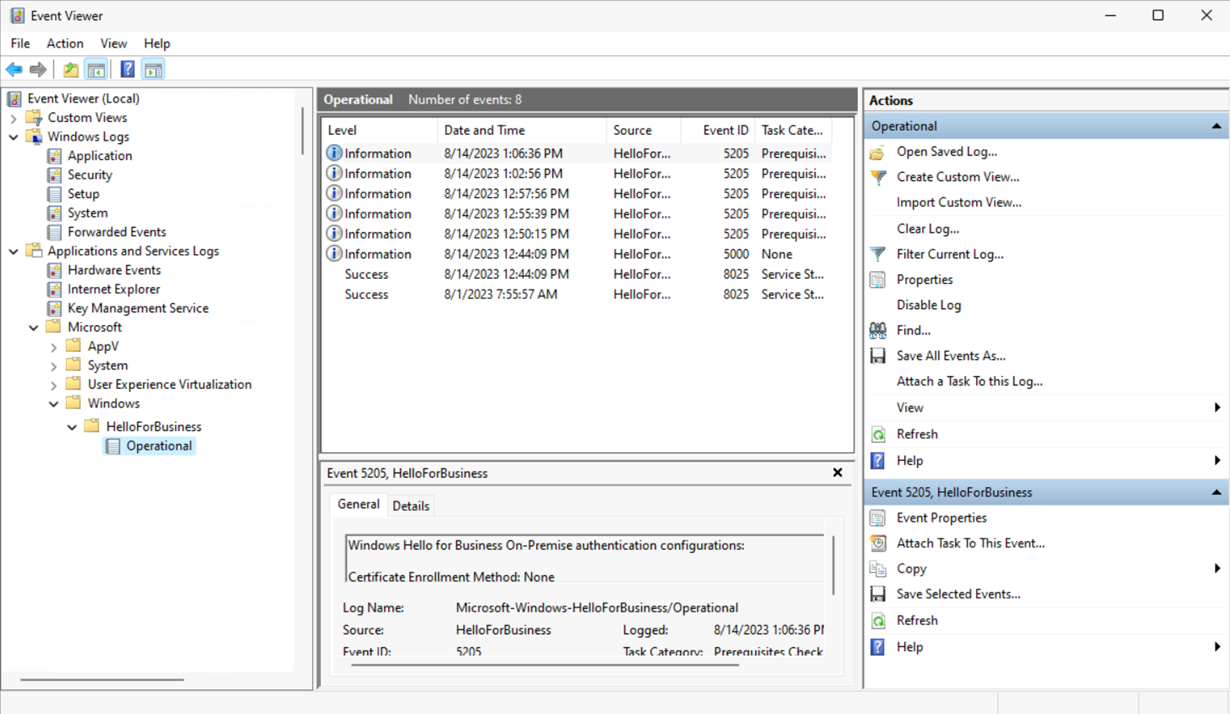
In case that you want to check the Event log for Windows Hello for Business issues you can find that at „Applications and Services Logs -> Microsoft -> Windows -> HelloForBusiness -> Operational“:
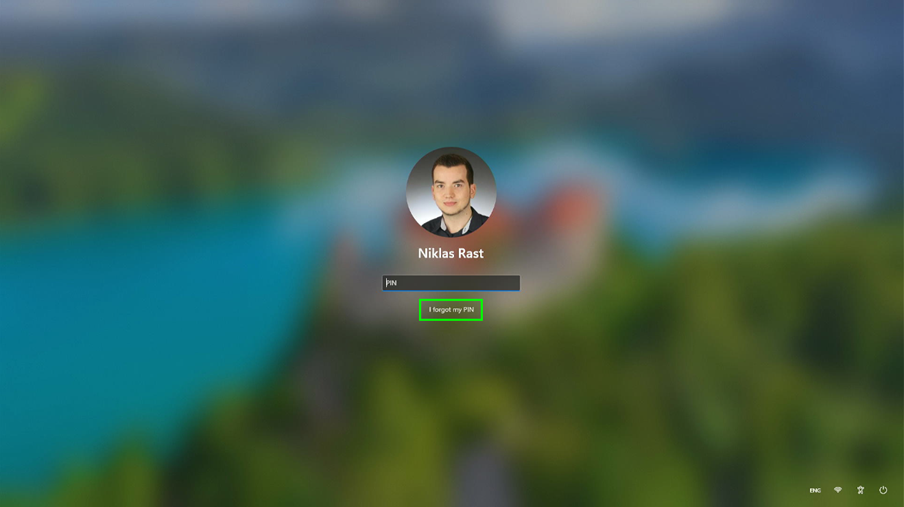
If a user forgets his PIN or the Biometrics does not work her can use the Self-Service from the Lock screen page of the device to click on „I forgot my PIN“ to initiate a reset by himself:
Once clicked there will popup an Azure AD authentication window where the User needs to sign in with his Azure AD credentials:
The user then can reset his PIN or biometrics by himself.
There are a few scenarios which are by design not supported and will not work:
-
Windows Server Active Directory Domain Services (AD DS)-joined (on-premises only devices) deployment.
-
Remote Desktop Protocol (RDP), virtual desktop infrastructure (VDI), and Citrix scenarios by using a security key.
-
S/MIME by using a security key.
-
Run as by using a security key.
-
Log in to a server by using a security key.
Conclusion
Windows Hello for Business Cloud Trust is a significant step forward in enhancing authentication security in hybrid environments. By integrating Cloud Trust, organizations can leverage the strengths of cloud services while maintaining a high level of trust and security. As the cyber threat landscape continues to evolve, adopting modern authentication mechanisms like Windows Hello for Business becomes imperative for organizations seeking to safeguard their data and systems effectively. Whether opting for Cloud Trust or Key Trust, the ultimate goal is to provide users with a seamless, secure, and password-free authentication experience that aligns with the organization’s security preferences. Cloud trust plays a pivotal role when the goal is a smooth integration between onprem and Cloud as it enables Single-Sign-ON capabilities and modern authentication with biometrics while keeping authentication data secure in hybrid environments.
If you want to distribute certificates you also need an working PKI infrastructure and an Intune NDES Connector.