A Comprehensive Guide to Setting Up Microsoft Defender for macOS: Strengthening Your System Security
31 December 2023
Configuring Defender for Endpoint on macOS devices
In the ever-evolving landscape of cybersecurity threats, protecting your macOS device from malicious software is of paramount importance. While Apple’s macOS comes equipped with robust built-in security features, it never hurts to add an extra layer of defense to safeguard your valuable data. Enter Microsoft Defender for macOS, a powerful and comprehensive security solution that brings Microsoft’s renowned expertise in threat detection and prevention to the macOS ecosystem. Throughout this blog post, I will delve into various aspects of setting up Microsoft Defender for macOS. We will cover the installation process, and essential configuration settings to maximize its effectiveness. We’ll also explore the key features and functionalities that make Microsoft Defender an indispensable tool in your cybersecurity arsenal.
Let’s dive in!
Intune Configuration Profiles
To setup Microsoft Defender for macOS we need to create a few Custom Configuration Profiles in Microsoft Intune. Follow those screenshots to create the profiles and assign them to your macOS device group.
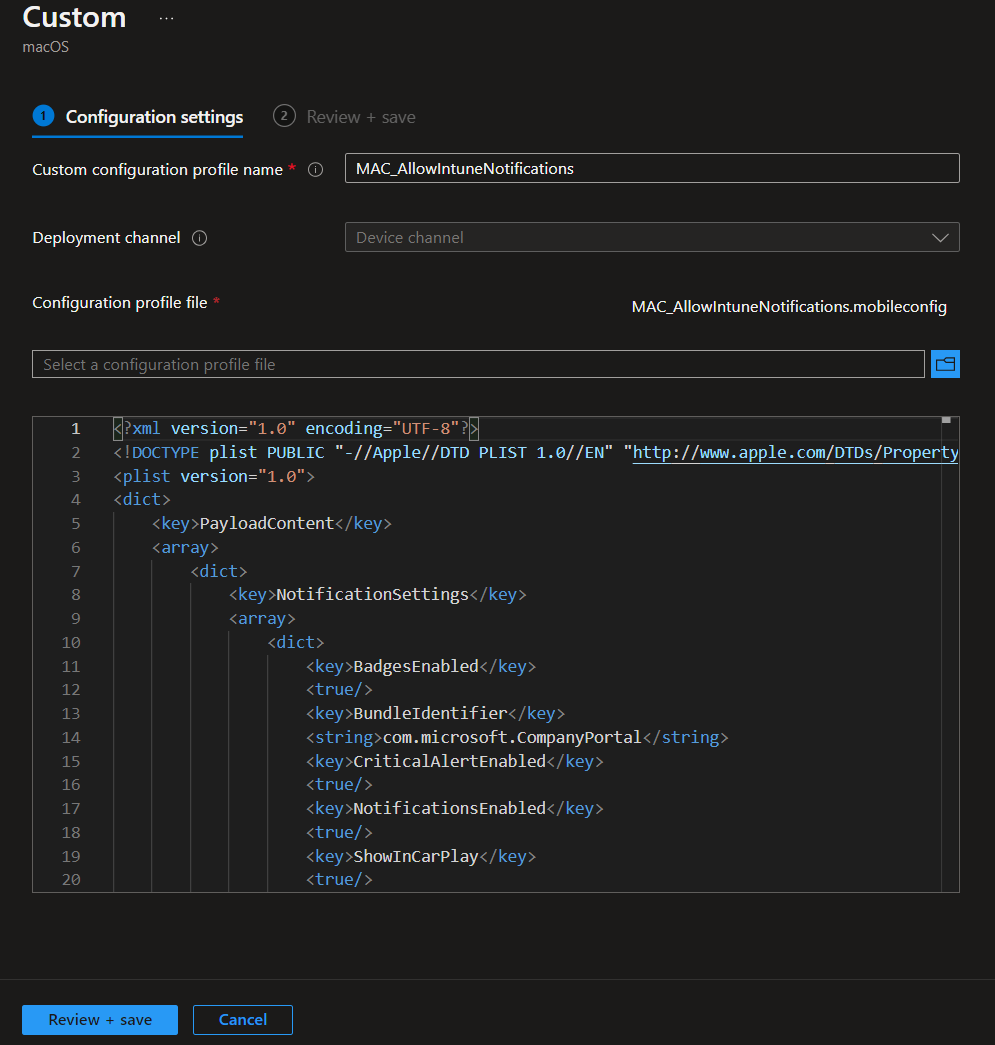
MAC_AllowIntuneNotifications
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>PayloadContent</key>
<array>
<dict>
<key>NotificationSettings</key>
<array>
<dict>
<key>BadgesEnabled</key>
<true/>
<key>BundleIdentifier</key>
<string>com.microsoft.CompanyPortal</string>
<key>CriticalAlertEnabled</key>
<true/>
<key>NotificationsEnabled</key>
<true/>
<key>ShowInCarPlay</key>
<true/>
<key>ShowInLockScreen</key>
<true/>
<key>ShowInNotificationCenter</key>
<true/>
<key>SoundsEnabled</key>
<true/>
</dict>
<dict>
<key>BadgesEnabled</key>
<true/>
<key>BundleIdentifier</key>
<string>com.microsoft.wdav</string>
<key>CriticalAlertEnabled</key>
<true/>
<key>NotificationsEnabled</key>
<true/>
<key>ShowInCarPlay</key>
<true/>
<key>ShowInLockScreen</key>
<true/>
<key>ShowInNotificationCenter</key>
<true/>
<key>SoundsEnabled</key>
<true/>
</dict>
<dict>
<key>BadgesEnabled</key>
<true/>
<key>BundleIdentifier</key>
<string>com.microsoft.intuneMDMAgent</string>
<key>CriticalAlertEnabled</key>
<true/>
<key>NotificationsEnabled</key>
<true/>
<key>ShowInCarPlay</key>
<true/>
<key>ShowInLockScreen</key>
<true/>
<key>ShowInNotificationCenter</key>
<true/>
<key>SoundsEnabled</key>
<true/>
</dict>
<dict>
<key>BadgesEnabled</key>
<true/>
<key>BundleIdentifier</key>
<string>com.microsoft.intuneMDMAgent.daemon</string>
<key>CriticalAlertEnabled</key>
<true/>
<key>NotificationsEnabled</key>
<true/>
<key>ShowInCarPlay</key>
<true/>
<key>ShowInLockScreen</key>
<true/>
<key>ShowInNotificationCenter</key>
<true/>
<key>SoundsEnabled</key>
<true/>
</dict>
<dict>
<key>BadgesEnabled</key>
<true/>
<key>BundleIdentifier</key>
<string>com.microsoft.Outlook</string>
<key>CriticalAlertEnabled</key>
<true/>
<key>NotificationsEnabled</key>
<true/>
<key>ShowInCarPlay</key>
<true/>
<key>ShowInLockScreen</key>
<true/>
<key>ShowInNotificationCenter</key>
<true/>
<key>SoundsEnabled</key>
<true/>
</dict>
<dict>
<key>BadgesEnabled</key>
<true/>
<key>BundleIdentifier</key>
<string>com.microsoft.teams</string>
<key>CriticalAlertEnabled</key>
<true/>
<key>NotificationsEnabled</key>
<true/>
<key>ShowInCarPlay</key>
<true/>
<key>ShowInLockScreen</key>
<true/>
<key>ShowInNotificationCenter</key>
<true/>
<key>SoundsEnabled</key>
<true/>
</dict>
<dict>
<key>BadgesEnabled</key>
<true/>
<key>BundleIdentifier</key>
<string>com.microsoft.CompanyPortalMac</string>
<key>CriticalAlertEnabled</key>
<true/>
<key>NotificationsEnabled</key>
<true/>
<key>ShowInCarPlay</key>
<true/>
<key>ShowInLockScreen</key>
<true/>
<key>ShowInNotificationCenter</key>
<true/>
<key>SoundsEnabled</key>
<true/>
</dict>
<dict>
<key>BadgesEnabled</key>
<true/>
<key>BundleIdentifier</key>
<string>com.microsoft.autoupdate2 </string>
<key>CriticalAlertEnabled</key>
<true/>
<key>NotificationsEnabled</key>
<true/>
<key>ShowInCarPlay</key>
<true/>
<key>ShowInLockScreen</key>
<true/>
<key>ShowInNotificationCenter</key>
<true/>
<key>SoundsEnabled</key>
<true/>
</dict>
<dict>
<key>BadgesEnabled</key>
<true/>
<key>BundleIdentifier</key>
<string>com.microsoft.autoupdate.fba</string>
<key>CriticalAlertEnabled</key>
<true/>
<key>NotificationsEnabled</key>
<true/>
<key>ShowInCarPlay</key>
<true/>
<key>ShowInLockScreen</key>
<true/>
<key>ShowInNotificationCenter</key>
<true/>
<key>SoundsEnabled</key>
<true/>
</dict>
<dict>
<key>BadgesEnabled</key>
<true/>
<key>BundleIdentifier</key>
<string>com.microsoft.edgemac</string>
<key>CriticalAlertEnabled</key>
<true/>
<key>NotificationsEnabled</key>
<true/>
<key>ShowInCarPlay</key>
<true/>
<key>ShowInLockScreen</key>
<true/>
<key>ShowInNotificationCenter</key>
<true/>
<key>SoundsEnabled</key>
<true/>
</dict>
<dict>
<key>BadgesEnabled</key>
<true/>
<key>BundleIdentifier</key>
<string>com.microsoft.OneDrive</string>
<key>CriticalAlertEnabled</key>
<false/>
<key>NotificationsEnabled</key>
<true/>
<key>ShowInCarPlay</key>
<true/>
<key>ShowInLockScreen</key>
<true/>
<key>ShowInNotificationCenter</key>
<true/>
<key>SoundsEnabled</key>
<true/>
</dict>
<dict>
<key>BadgesEnabled</key>
<true/>
<key>BundleIdentifier</key>
<string>com.microsoft.Word </string>
<key>CriticalAlertEnabled</key>
<false/>
<key>NotificationsEnabled</key>
<true/>
<key>ShowInCarPlay</key>
<true/>
<key>ShowInLockScreen</key>
<true/>
<key>ShowInNotificationCenter</key>
<true/>
<key>SoundsEnabled</key>
<true/>
</dict>
<dict>
<key>BadgesEnabled</key>
<true/>
<key>BundleIdentifier</key>
<string>com.microsoft.Excel </string>
<key>CriticalAlertEnabled</key>
<false/>
<key>NotificationsEnabled</key>
<true/>
<key>ShowInCarPlay</key>
<true/>
<key>ShowInLockScreen</key>
<true/>
<key>ShowInNotificationCenter</key>
<true/>
<key>SoundsEnabled</key>
<true/>
</dict>
<dict>
<key>BadgesEnabled</key>
<true/>
<key>BundleIdentifier</key>
<string>com.microsoft.Powerpoint </string>
<key>CriticalAlertEnabled</key>
<false/>
<key>NotificationsEnabled</key>
<true/>
<key>ShowInCarPlay</key>
<true/>
<key>ShowInLockScreen</key>
<true/>
<key>ShowInNotificationCenter</key>
<true/>
<key>SoundsEnabled</key>
<true/>
</dict>
<dict>
<key>BadgesEnabled</key>
<true/>
<key>BundleIdentifier</key>
<string>com.microsoft.onenote.mac</string>
<key>CriticalAlertEnabled</key>
<false/>
<key>NotificationsEnabled</key>
<true/>
<key>ShowInCarPlay</key>
<true/>
<key>ShowInLockScreen</key>
<true/>
<key>ShowInNotificationCenter</key>
<true/>
<key>SoundsEnabled</key>
<true/>
</dict>
<dict>
<key>BadgesEnabled</key>
<true/>
<key>BundleIdentifier</key>
<string>com.microsoft.OneDrive</string>
<key>CriticalAlertEnabled</key>
<false/>
<key>NotificationsEnabled</key>
<true/>
<key>ShowInCarPlay</key>
<true/>
<key>ShowInLockScreen</key>
<true/>
<key>ShowInNotificationCenter</key>
<true/>
<key>SoundsEnabled</key>
<true/>
</dict>
<dict>
<key>BadgesEnabled</key>
<true/>
<key>BundleIdentifier</key>
<string>com.microsoft.rdc.macos</string>
<key>CriticalAlertEnabled</key>
<false/>
<key>NotificationsEnabled</key>
<true/>
<key>ShowInCarPlay</key>
<true/>
<key>ShowInLockScreen</key>
<true/>
<key>ShowInNotificationCenter</key>
<true/>
<key>SoundsEnabled</key>
<true/>
</dict>
<dict>
<key>BadgesEnabled</key>
<true/>
<key>BundleIdentifier</key>
<string>com.microsoft.VSCode</string>
<key>CriticalAlertEnabled</key>
<false/>
<key>NotificationsEnabled</key>
<true/>
<key>ShowInCarPlay</key>
<true/>
<key>ShowInLockScreen</key>
<true/>
<key>ShowInNotificationCenter</key>
<true/>
<key>SoundsEnabled</key>
<true/>
</dict>
<dict>
<key>BadgesEnabled</key>
<true/>
<key>BundleIdentifier</key>
<string>com.microsoft.wdav.tray</string>
<key>CriticalAlertEnabled</key>
<true/>
<key>NotificationsEnabled</key>
<true/>
<key>ShowInCarPlay</key>
<true/>
<key>ShowInLockScreen</key>
<true/>
<key>ShowInNotificationCenter</key>
<true/>
<key>SoundsEnabled</key>
<true/>
</dict>
</array>
<key>PayloadDisplayName</key>
<string>Notifications</string>
<key>PayloadIdentifier</key>
<string>com.apple.notificationsettings</string>
<key>PayloadType</key>
<string>com.apple.notificationsettings</string>
<key>PayloadUUID</key>
<string>8FC45A38-886E-48B0-966F-05F15EEC8DD0</string>
<key>PayloadVersion</key>
<integer>1</integer>
</dict>
</array>
<key>PayloadDisplayName</key>
<string>Notifications for Intune, Defender and Office</string>
<key>PayloadIdentifier</key>
<string>0B76A486-E9B0-45B2-B088-71F2FD3738E1</string>
<key>PayloadType</key>
<string>Configuration</string>
<key>PayloadUUID</key>
<string>D6F21A2A-BD1B-4D2C-AF9E-54AA3874A1EE</string>
<key>PayloadVersion</key>
<integer>1</integer>
</dict>
</plist>
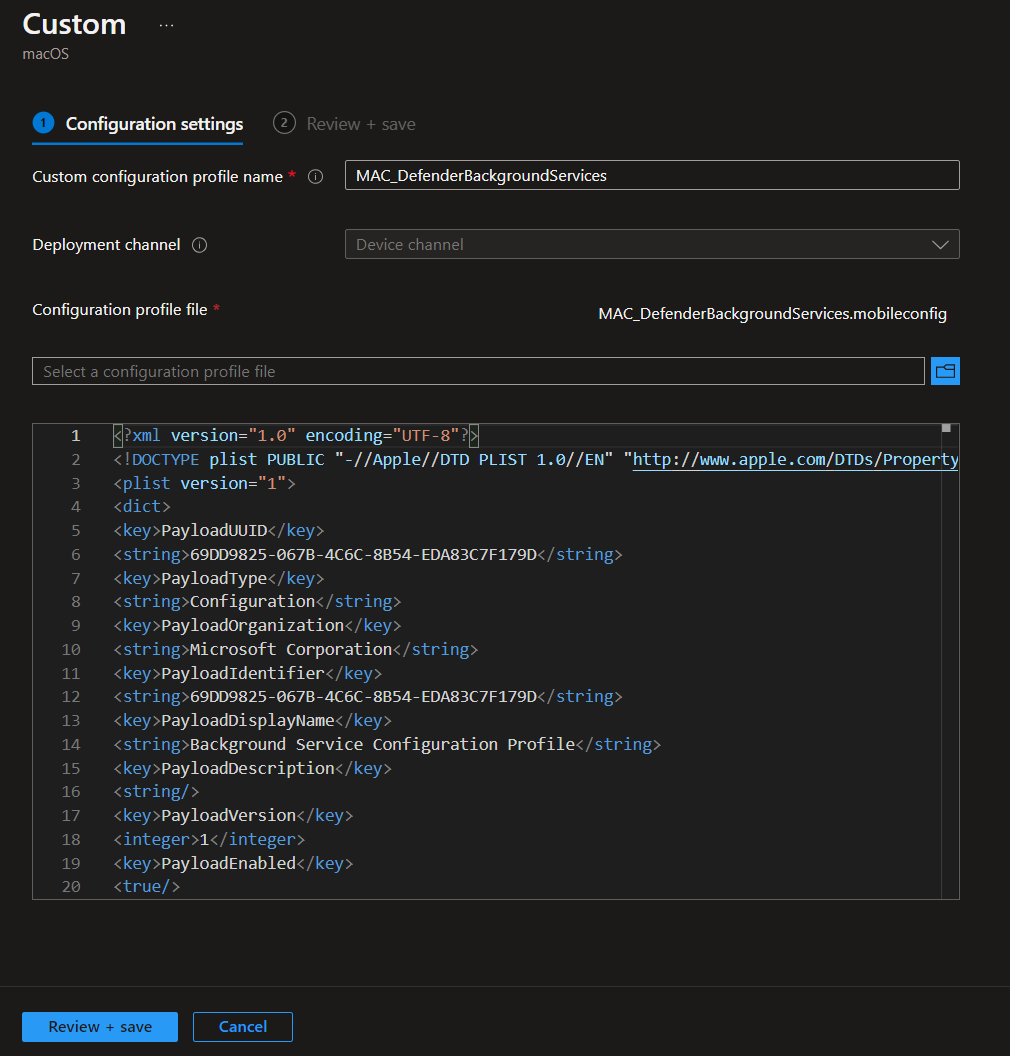
MAC_DefenderBackgroundServices
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1">
<dict>
<key>PayloadUUID</key>
<string>69DD9825-067B-4C6C-8B54-EDA83C7F179D</string>
<key>PayloadType</key>
<string>Configuration</string>
<key>PayloadOrganization</key>
<string>Microsoft Corporation</string>
<key>PayloadIdentifier</key>
<string>69DD9825-067B-4C6C-8B54-EDA83C7F179D</string>
<key>PayloadDisplayName</key>
<string>Background Service Configuration Profile</string>
<key>PayloadDescription</key>
<string/>
<key>PayloadVersion</key>
<integer>1</integer>
<key>PayloadEnabled</key>
<true/>
<key>PayloadRemovalDisallowed</key>
<true/>
<key>PayloadScope</key>
<string>System</string>
<key>PayloadContent</key>
<array>
<dict>
<key>PayloadDescription</key>
<string>Background Service Management for Microsoft Defender</string>
<key>PayloadIdentifier</key>
<string>4DB96276-2310-44C2-AE11-C6E761FB0304.privacy.04102481-C1F1-44F2-B548-E0B554890493</string>
<key>PayloadUUID</key>
<string>A9BF8FA9-CEA3-42A2-B8C1-E1998B84CBB0</string>
<key>Rules</key>
<array>
<dict>
<key>RuleType</key>
<string>LabelPrefix</string>
<key>RuleValue</key>
<string>com.microsoft.fresno</string>
</dict>
<dict>
<key>RuleType</key>
<string>LabelPrefix</string>
<key>RuleValue</key>
<string>com.microsoft.dlp</string>
</dict>
</array>
<key>PayloadType</key>
<string>com.apple.servicemanagement</string>
<key>PayloadDisplayName</key>
<string>Background Service Management for Microsoft Defender</string>
</dict>
</array>
</dict>
</plist>
MAC_DefenderExtensions
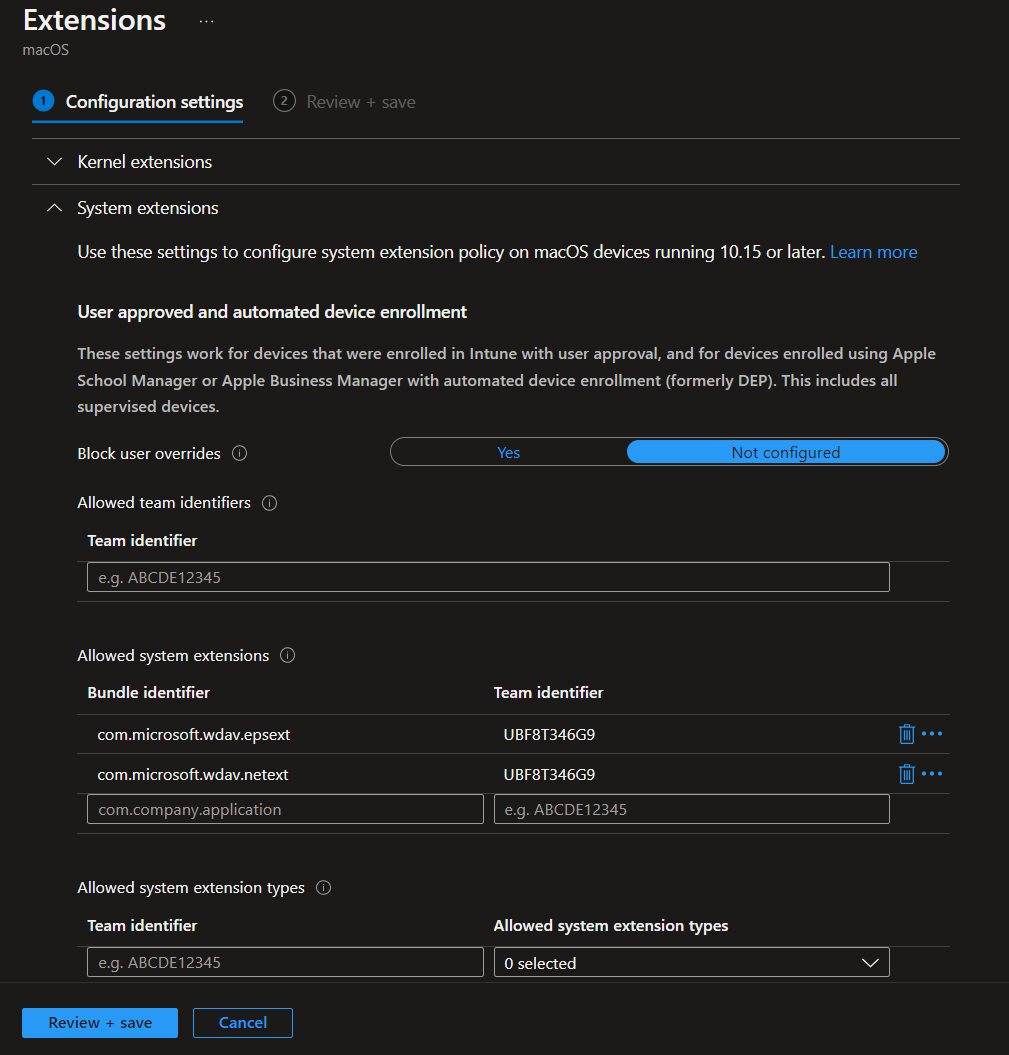
System extensions:
- com.microsoft.wdav.epsext == UBF8T346G9
- com.microsoft.wdav.netext == UBF8T346G9
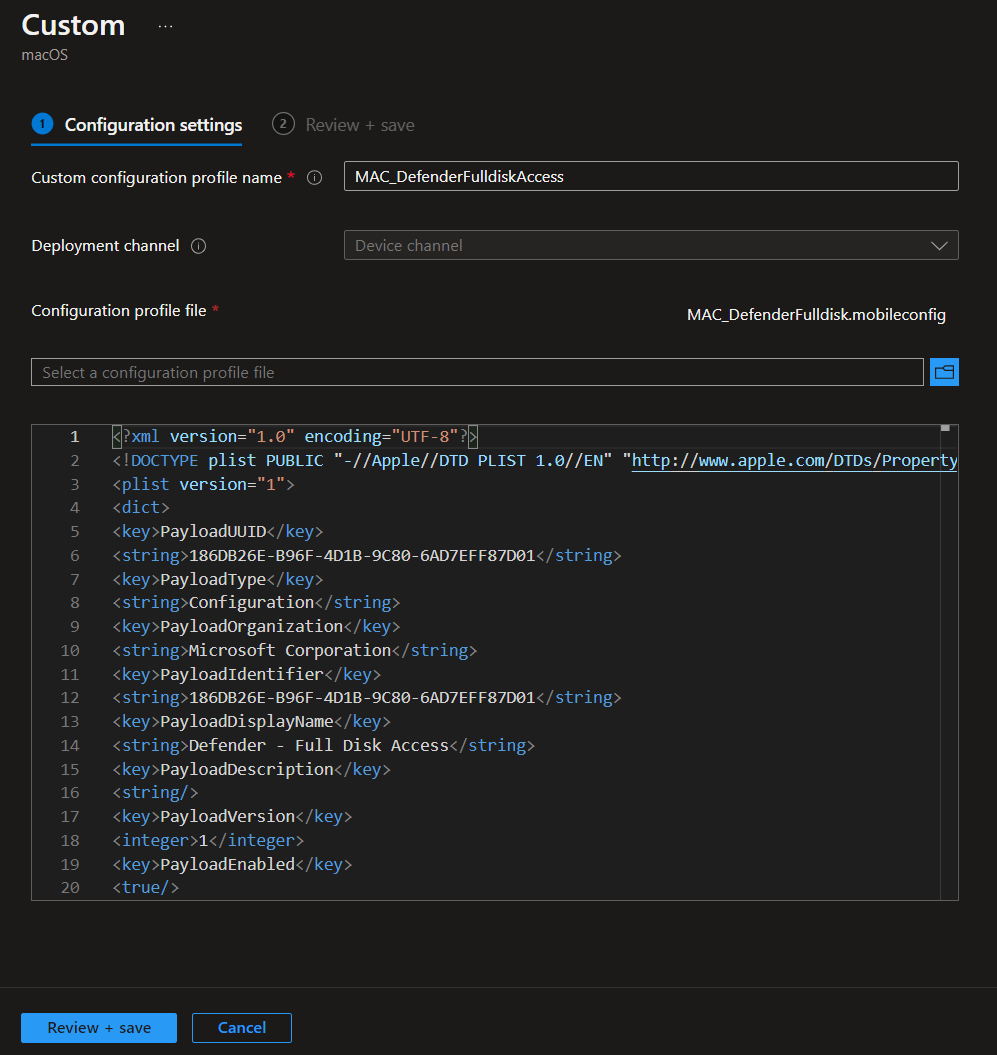
MAC_DefenderFulldiskAccess
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1">
<dict>
<key>PayloadUUID</key>
<string>186DB26E-B96F-4D1B-9C80-6AD7EFF87D01</string>
<key>PayloadType</key>
<string>Configuration</string>
<key>PayloadOrganization</key>
<string>Microsoft Corporation</string>
<key>PayloadIdentifier</key>
<string>186DB26E-B96F-4D1B-9C80-6AD7EFF87D01</string>
<key>PayloadDisplayName</key>
<string>Defender - Full Disk Access</string>
<key>PayloadDescription</key>
<string/>
<key>PayloadVersion</key>
<integer>1</integer>
<key>PayloadEnabled</key>
<true/>
<key>PayloadRemovalDisallowed</key>
<true/>
<key>PayloadScope</key>
<string>System</string>
<key>PayloadContent</key>
<array>
<dict>
<key>PayloadUUID</key>
<string>782EFFBA-A158-4571-822D-D085BA43ED7A</string>
<key>PayloadType</key>
<string>com.apple.TCC.configuration-profile-policy</string>
<key>PayloadOrganization</key>
<string>Microsoft Corporation</string>
<key>PayloadIdentifier</key>
<string>782EFFBA-A158-4571-822D-D085BA43ED7A</string>
<key>PayloadDisplayName</key>
<string>Privacy Preferences Policy Control</string>
<key>PayloadDescription</key>
<string/>
<key>PayloadVersion</key>
<integer>1</integer>
<key>PayloadEnabled</key>
<true/>
<key>Services</key>
<dict>
<key>SystemPolicyAllFiles</key>
<array>
<dict>
<key>Identifier</key>
<string>com.microsoft.wdav</string>
<key>CodeRequirement</key>
<string>identifier "com.microsoft.wdav" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = UBF8T346G9</string>
<key>IdentifierType</key>
<string>bundleID</string>
<key>StaticCode</key>
<integer>0</integer>
<key>Allowed</key>
<integer>1</integer>
</dict>
<dict>
<key>Identifier</key>
<string>com.microsoft.wdav.epsext</string>
<key>CodeRequirement</key>
<string>identifier "com.microsoft.wdav.epsext" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = UBF8T346G9</string>
<key>IdentifierType</key>
<string>bundleID</string>
<key>StaticCode</key>
<integer>0</integer>
<key>Allowed</key>
<integer>1</integer>
</dict>
<dict>
<key>Identifier</key>
<string>com.microsoft.dlp.daemon</string>
<key>CodeRequirement</key>
<string>identifier "com.microsoft.dlp.daemon" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = UBF8T346G9</string>
<key>IdentifierType</key>
<string>bundleID</string>
<key>StaticCode</key>
<integer>0</integer>
<key>Allowed</key>
<integer>1</integer>
</dict>
</array>
</dict>
</dict>
</array>
</dict>
</plist>
MAC_DefenderNetworkfilter
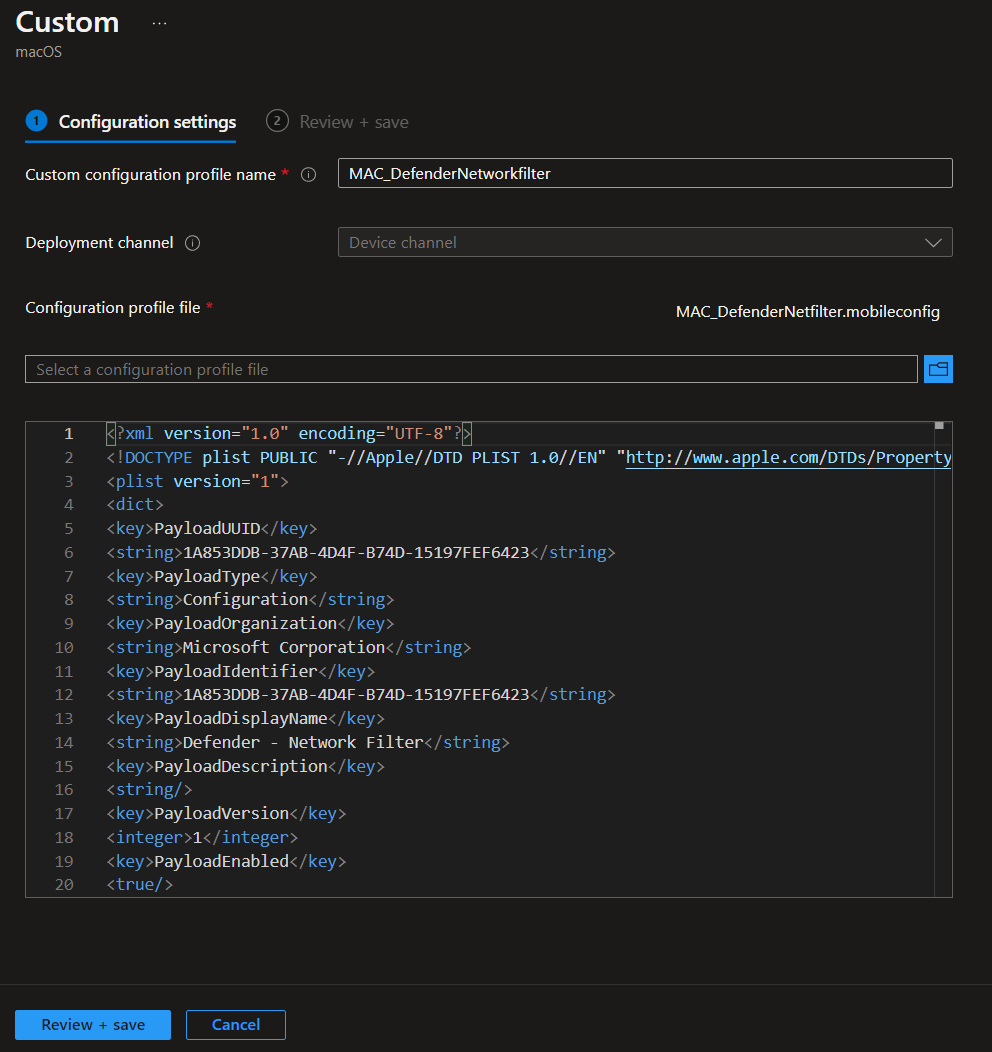
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1">
<dict>
<key>PayloadUUID</key>
<string>1A853DDB-37AB-4D4F-B74D-15197FEF6423</string>
<key>PayloadType</key>
<string>Configuration</string>
<key>PayloadOrganization</key>
<string>Microsoft Corporation</string>
<key>PayloadIdentifier</key>
<string>1A853DDB-37AB-4D4F-B74D-15197FEF6423</string>
<key>PayloadDisplayName</key>
<string>Defender - Network Filter</string>
<key>PayloadDescription</key>
<string/>
<key>PayloadVersion</key>
<integer>1</integer>
<key>PayloadEnabled</key>
<true/>
<key>PayloadRemovalDisallowed</key>
<true/>
<key>PayloadScope</key>
<string>System</string>
<key>PayloadContent</key>
<array>
<dict>
<key>FilterDataProviderBundleIdentifier</key>
<string>com.microsoft.wdav.netext</string>
<key>FilterDataProviderDesignatedRequirement</key>
<string>identifier "com.microsoft.wdav.netext" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = UBF8T346G9</string>
<key>FilterGrade</key>
<string>inspector</string>
<key>FilterPackets</key>
<false/>
<key>FilterSockets</key>
<true/>
<key>FilterType</key>
<string>Plugin</string>
<key>PayloadDisplayName</key>
<string>Web Content Filter Payload</string>
<key>PayloadIdentifier</key>
<string>283F4BF0-788A-4435-9B62-3E00896358D7</string>
<key>PayloadOrganization</key>
<string>JAMF Software</string>
<key>PayloadType</key>
<string>com.apple.webcontent-filter</string>
<key>PayloadUUID</key>
<string>283F4BF0-788A-4435-9B62-3E00896358D7</string>
<key>PayloadVersion</key>
<integer>1</integer>
<key>PluginBundleID</key>
<string>com.microsoft.wdav</string>
<key>UserDefinedName</key>
<string>Microsoft Defender Content Filter</string>
</dict>
</array>
</dict>
</plist>
MAC_DefenderNetworkfilter
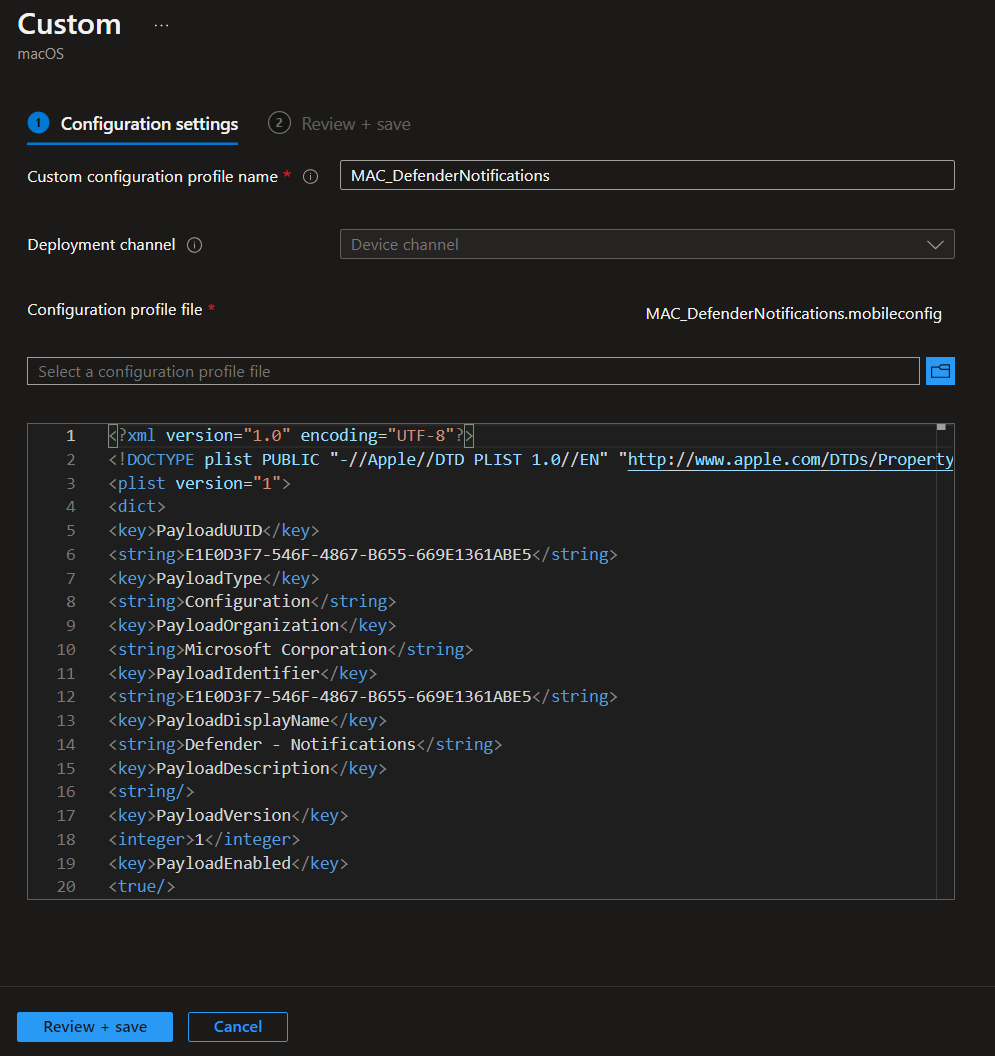
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1">
<dict>
<key>PayloadUUID</key>
<string>E1E0D3F7-546F-4867-B655-669E1361ABE5</string>
<key>PayloadType</key>
<string>Configuration</string>
<key>PayloadOrganization</key>
<string>Microsoft Corporation</string>
<key>PayloadIdentifier</key>
<string>E1E0D3F7-546F-4867-B655-669E1361ABE5</string>
<key>PayloadDisplayName</key>
<string>Defender - Notifications</string>
<key>PayloadDescription</key>
<string/>
<key>PayloadVersion</key>
<integer>1</integer>
<key>PayloadEnabled</key>
<true/>
<key>PayloadRemovalDisallowed</key>
<true/>
<key>PayloadScope</key>
<string>System</string>
<key>PayloadContent</key>
<array>
<dict>
<key>PayloadDisplayName</key>
<string>Notifications Payload</string>
<key>PayloadIdentifier</key>
<string>05BF7221-2470-477D-99B3-1729B1932BDB</string>
<key>PayloadOrganization</key>
<string>Microsoft Corporation</string>
<key>PayloadType</key>
<string>com.apple.notificationsettings</string>
<key>PayloadUUID</key>
<string>05BF7221-2470-477D-99B3-1729B1932BDB</string>
<key>PayloadVersion</key>
<integer>1</integer>
<key>NotificationSettings</key>
<array>
<dict>
<key>AlertType</key>
<integer>1</integer>
<key>BadgesEnabled</key>
<true/>
<key>BundleIdentifier</key>
<string>com.microsoft.autoupdate2</string>
<key>CriticalAlertEnabled</key>
<false/>
<key>NotificationsEnabled</key>
<true/>
<key>ShowInLockScreen</key>
<false/>
<key>ShowInNotificationCenter</key>
<true/>
<key>SoundsEnabled</key>
<true/>
</dict>
<dict>
<key>AlertType</key>
<integer>1</integer>
<key>BadgesEnabled</key>
<true/>
<key>BundleIdentifier</key>
<string>com.microsoft.wdav.tray</string>
<key>CriticalAlertEnabled</key>
<false/>
<key>NotificationsEnabled</key>
<true/>
<key>ShowInLockScreen</key>
<false/>
<key>ShowInNotificationCenter</key>
<true/>
<key>SoundsEnabled</key>
<true/>
</dict>
</array>
</dict>
</array>
</dict>
</plist>
MAC_DefenderOnboarding
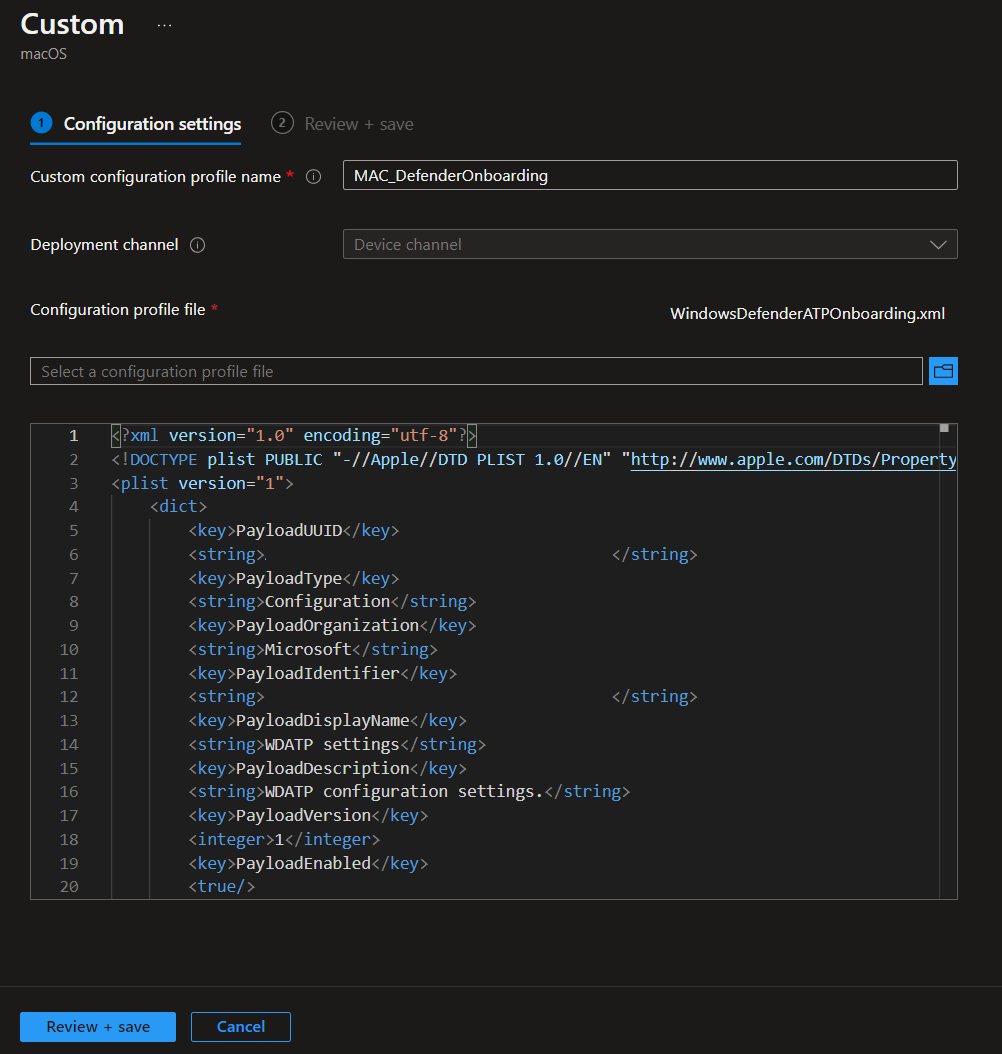
You need to download your tenant-custom XML File from the Microsoft Security Portal (https://security.microsoft.com/) go to Settings an under Defender for Endpoint in the Onboarding blade choose macOS and download the Onboarding package. Within the .ZIP file you will find your tenant-custom XML file with the right settings. The XML file will look similar to this sample:
<?xml version="1.0" encoding="utf-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1">
<dict>
<key>PayloadUUID</key>
<string>XXXXXXXXXXXXXXXXX</string>
<key>PayloadType</key>
<string>Configuration</string>
<key>PayloadOrganization</key>
<string>Microsoft</string>
<key>PayloadIdentifier</key>
<string>XXXXXXXXXXXXXXXXX</string>
<key>PayloadDisplayName</key>
<string>WDATP settings</string>
<key>PayloadDescription</key>
<string>WDATP configuration settings.</string>
<key>PayloadVersion</key>
<integer>1</integer>
<key>PayloadEnabled</key>
<true/>
<key>PayloadRemovalDisallowed</key>
<true/>
<key>PayloadScope</key>
<string>System</string>
<key>PayloadContent</key>
<array>
<dict>
<key>PayloadUUID</key>
<string>XXXXXXXXXXXXXXXXX</string>
<key>PayloadType</key>
<string>com.microsoft.wdav.atp</string>
<key>PayloadOrganization</key>
<string>Microsoft</string>
<key>PayloadIdentifier</key>
<string>XXXXXXXXXXXXXXXXX</string>
<key>PayloadDisplayName</key>
<string>WDATP configuration settings</string>
<key>PayloadDescription</key>
<string/>
<key>PayloadVersion</key>
<integer>1</integer>
<key>PayloadEnabled</key>
<true/>
<key>AllowUserOverrides</key>
<true/>
<key>OrgId</key>
<string>XXXXXXXXXXXXXXXXX</string>
<key>OnboardingInfo</key>
<string>XXXXXXXXXXXXXXXXX</string>
</dict>
</array>
</dict>
</plist>
MAC_DefenderUpdates
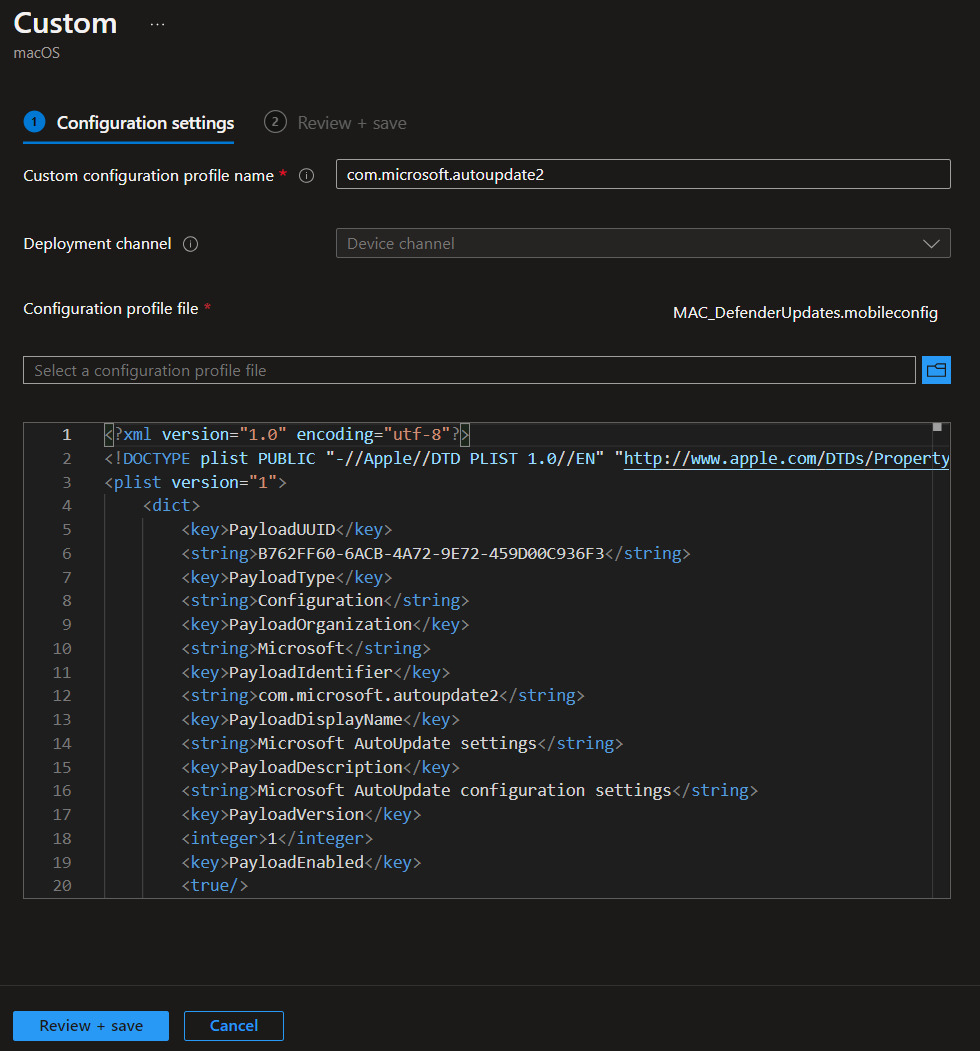
<?xml version="1.0" encoding="utf-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1">
<dict>
<key>PayloadUUID</key>
<string>B762FF60-6ACB-4A72-9E72-459D00C936F3</string>
<key>PayloadType</key>
<string>Configuration</string>
<key>PayloadOrganization</key>
<string>Microsoft</string>
<key>PayloadIdentifier</key>
<string>com.microsoft.autoupdate2</string>
<key>PayloadDisplayName</key>
<string>Microsoft AutoUpdate settings</string>
<key>PayloadDescription</key>
<string>Microsoft AutoUpdate configuration settings</string>
<key>PayloadVersion</key>
<integer>1</integer>
<key>PayloadEnabled</key>
<true/>
<key>PayloadRemovalDisallowed</key>
<true/>
<key>PayloadScope</key>
<string>System</string>
<key>PayloadContent</key>
<array>
<dict>
<key>PayloadUUID</key>
<string>5A6F350A-CC2C-440B-A074-68E3F34EBAE9</string>
<key>PayloadType</key>
<string>com.microsoft.autoupdate2</string>
<key>PayloadOrganization</key>
<string>Microsoft</string>
<key>PayloadIdentifier</key>
<string>com.microsoft.autoupdate2</string>
<key>PayloadDisplayName</key>
<string>Microsoft AutoUpdate configuration settings</string>
<key>PayloadDescription</key>
<string/>
<key>PayloadVersion</key>
<integer>1</integer>
<key>PayloadEnabled</key>
<true/>
<key>ChannelName</key>
<string>Current</string>
<key>HowToCheck</key>
<string>AutomaticDownload</string>
<key>EnableCheckForUpdatesButton</key>
<true/>
<key>DisableInsiderCheckbox</key>
<false/>
</dict>
</array>
</dict>
</plist>
Intune Scripts
You should add some Shell Scripts to manage the scheduled scans for Defender on macOS. Those scripts are from the Microsoft repository https://github.com/microsoft/shell-intune-samples/tree/master/macOS/Config/MDATP. In the repository you will find also all XML files and additional configs.
DefenderQuickScan
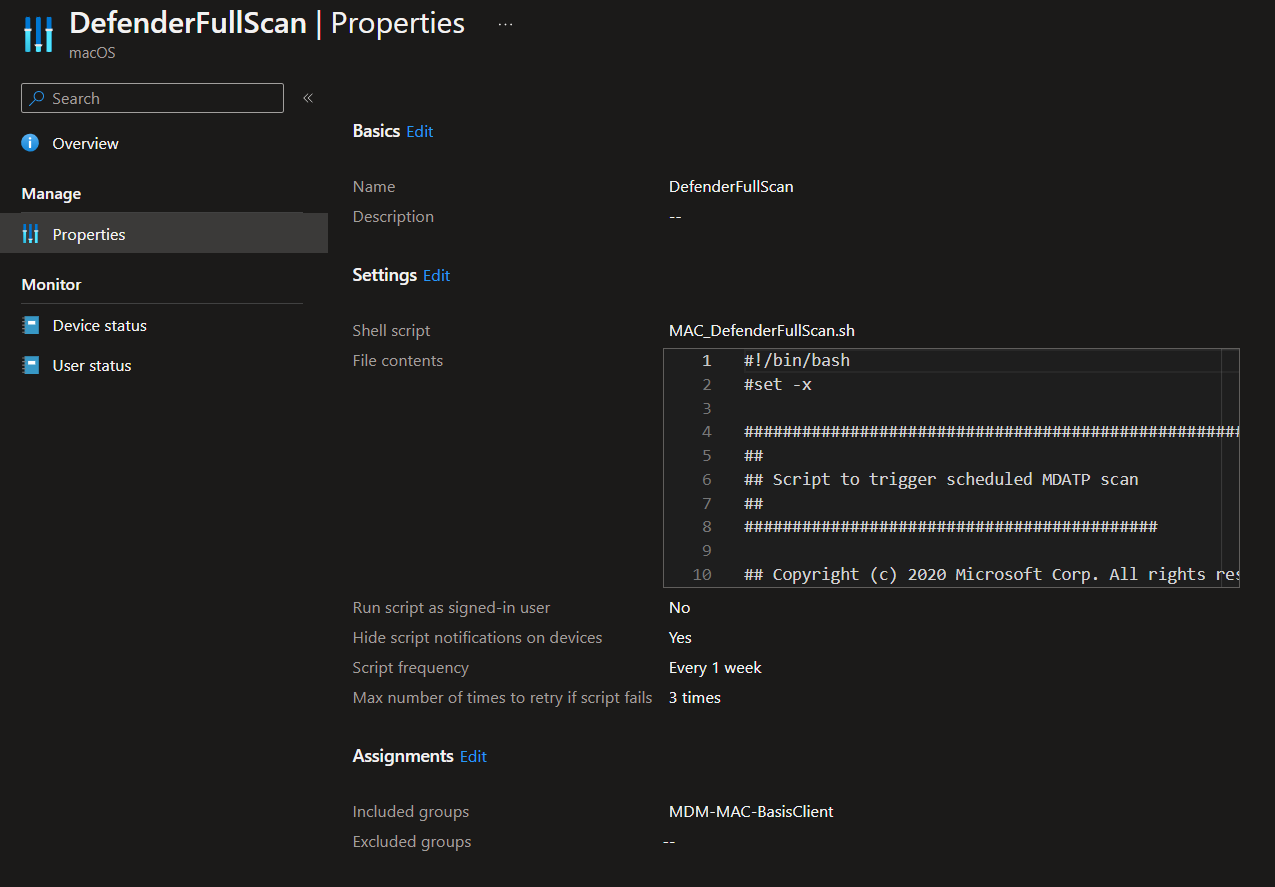
SHELL Script:
#!/bin/bash
#set -x
############################################################################################
##
## Script to trigger scheduled MDATP scan
##
###########################################
## Copyright (c) 2020 Microsoft Corp. All rights reserved.
## Scripts are not supported under any Microsoft standard support program or service. The scripts are provided AS IS without warranty of any kind.
## Microsoft disclaims all implied warranties including, without limitation, any implied warranties of merchantability or of fitness for a
## particular purpose. The entire risk arising out of the use or performance of the scripts and documentation remains with you. In no event shall
## Microsoft, its authors, or anyone else involved in the creation, production, or delivery of the scripts be liable for any damages whatsoever
## (including, without limitation, damages for loss of business profits, business interruption, loss of business information, or other pecuniary
## loss) arising out of the use of or inability to use the sample scripts or documentation, even if Microsoft has been advised of the possibility
## of such damages.
## Feedback: neiljohn@microsoft.com
# Define variables
log="/var/log/mdatpscheduledscan.log"
appname="Scheduled MDATP Scan"
exec 1>> $log 2>&1
echo ""
echo "##############################################################"
echo "# $(date) | Starting $appname"
echo "############################################################"
echo ""
/usr/local/bin/mdatp full quick >/dev/null
DefenderQuickScan
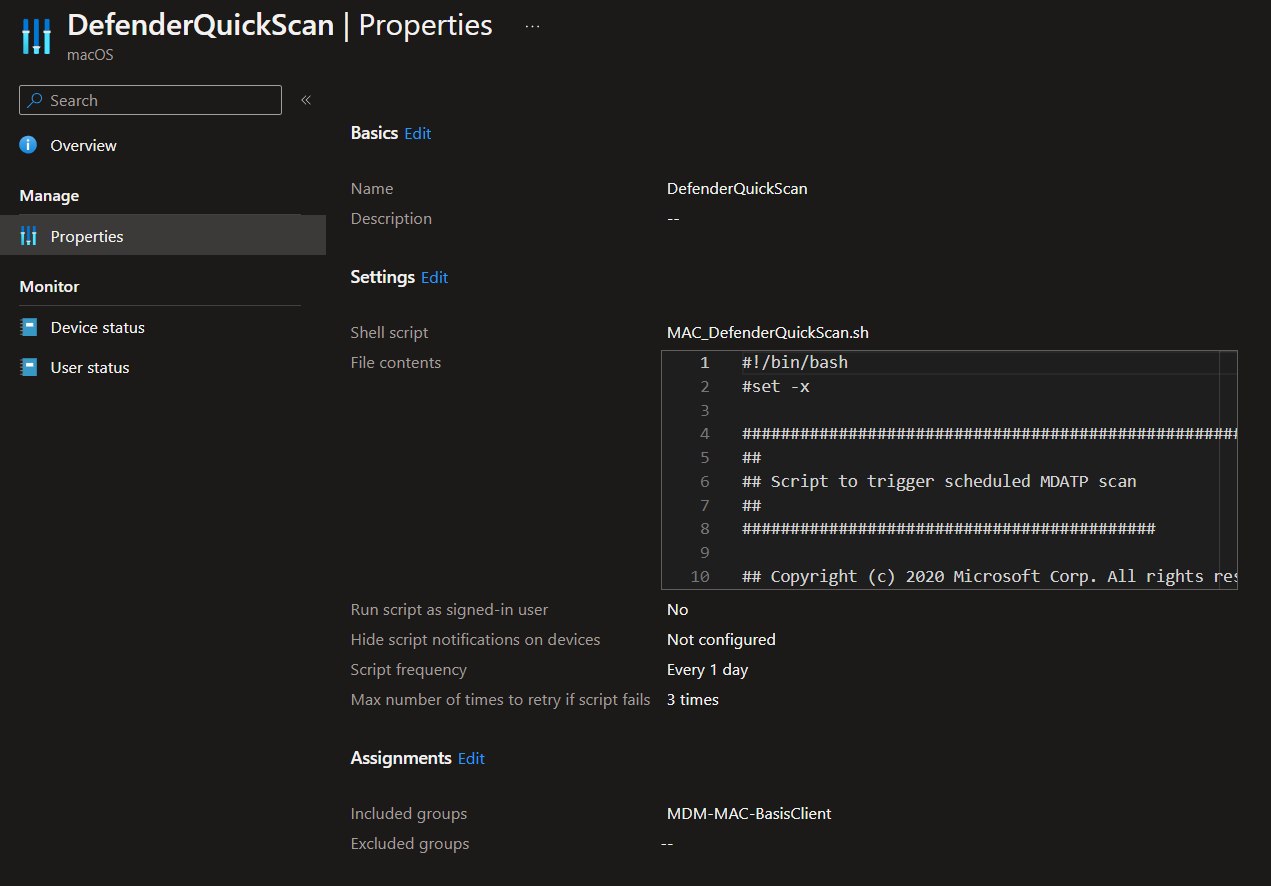
#!/bin/bash
#set -x
############################################################################################
##
## Script to trigger scheduled MDATP scan
##
###########################################
## Copyright (c) 2020 Microsoft Corp. All rights reserved.
## Scripts are not supported under any Microsoft standard support program or service. The scripts are provided AS IS without warranty of any kind.
## Microsoft disclaims all implied warranties including, without limitation, any implied warranties of merchantability or of fitness for a
## particular purpose. The entire risk arising out of the use or performance of the scripts and documentation remains with you. In no event shall
## Microsoft, its authors, or anyone else involved in the creation, production, or delivery of the scripts be liable for any damages whatsoever
## (including, without limitation, damages for loss of business profits, business interruption, loss of business information, or other pecuniary
## loss) arising out of the use of or inability to use the sample scripts or documentation, even if Microsoft has been advised of the possibility
## of such damages.
## Feedback: neiljohn@microsoft.com
# Define variables
log="/var/log/mdatpscheduledscan.log"
appname="Scheduled MDATP Scan"
exec 1>> $log 2>&1
echo ""
echo "##############################################################"
echo "# $(date) | Starting $appname"
echo "############################################################"
echo ""
/usr/local/bin/mdatp scan quick >/dev/null
Defender Configuration Profiles
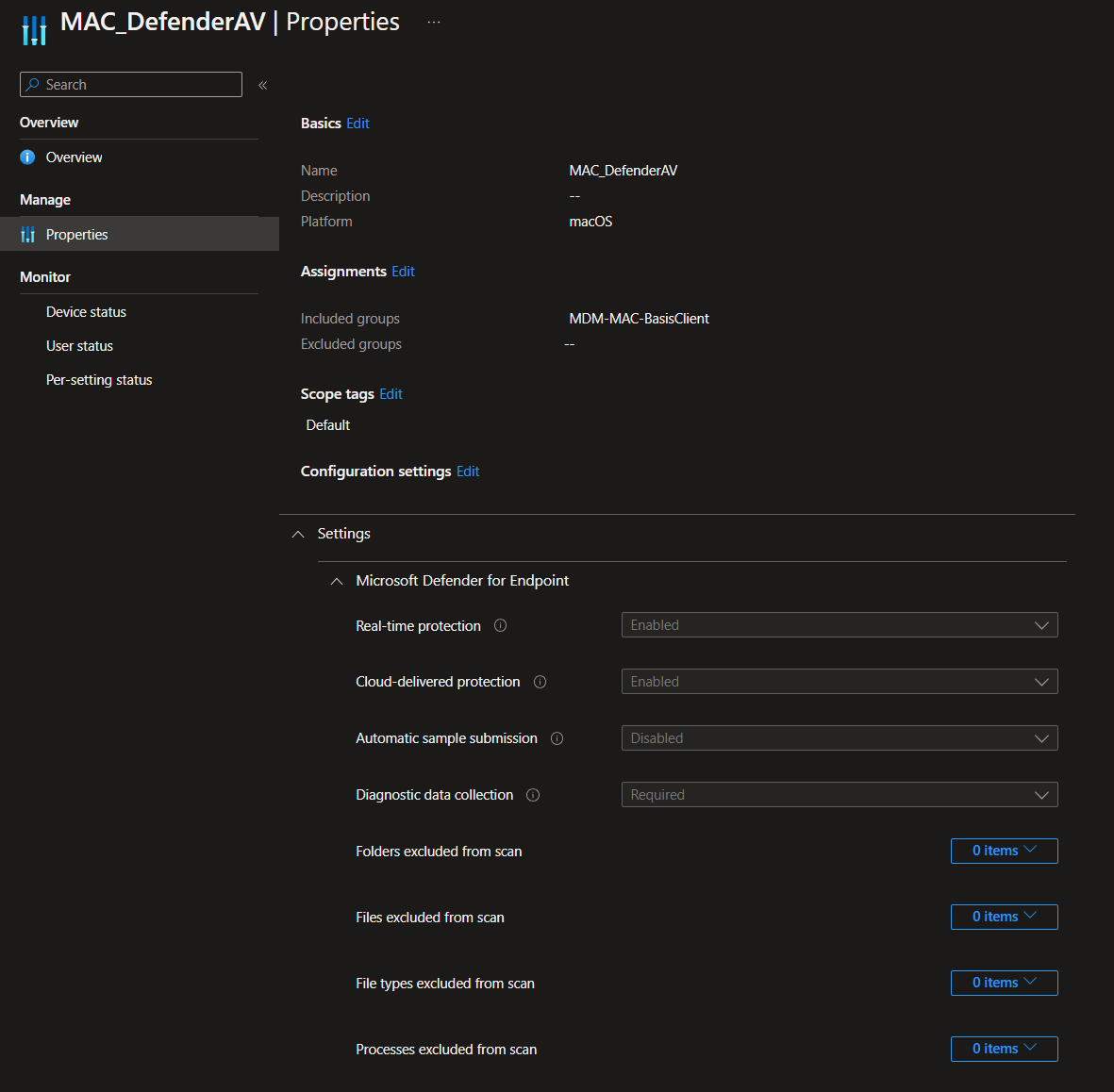
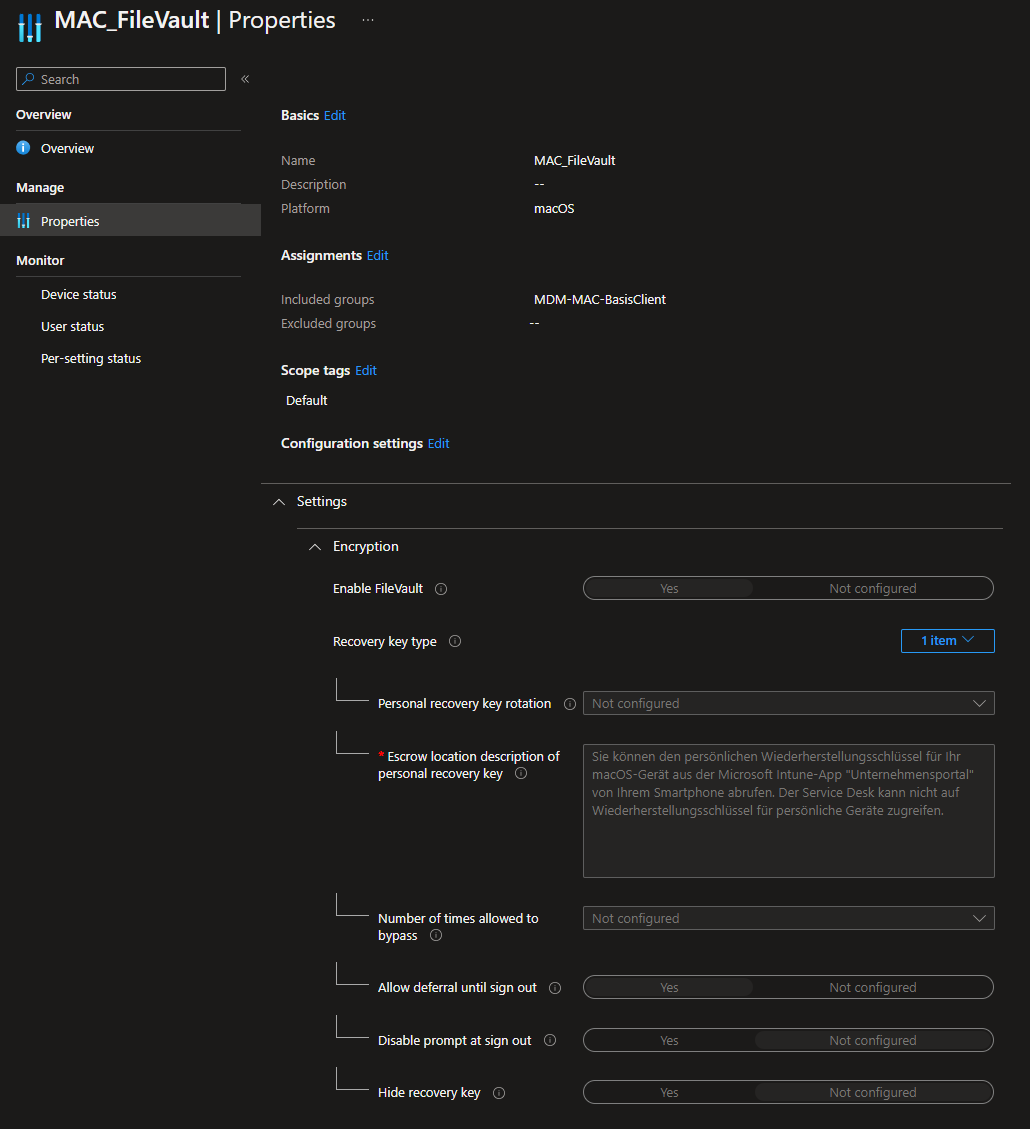
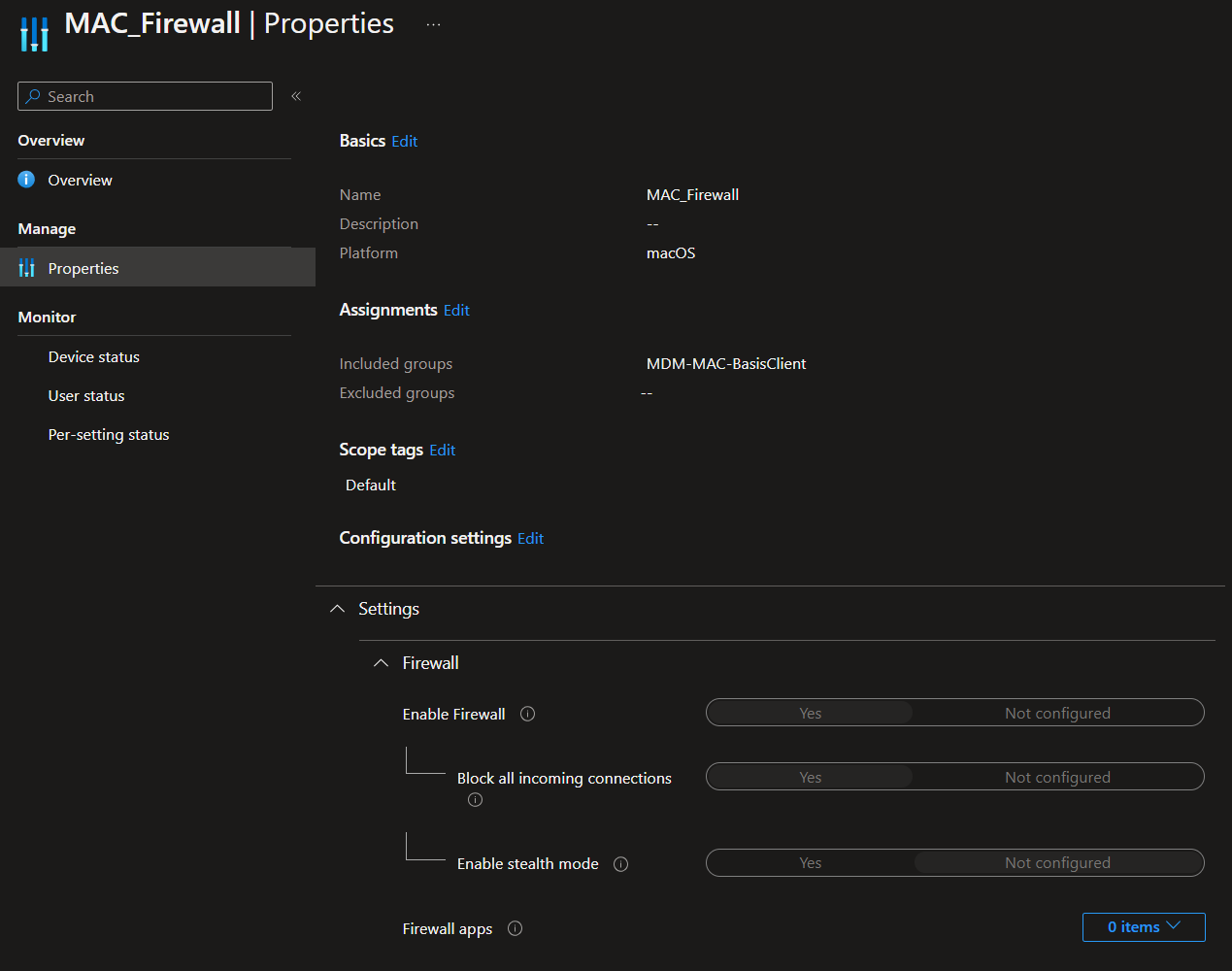
Lastly you need to configure the Defender Anti-Virus (AV) engine, disk-encryption and firewall with Intune Endpoint Protection configuration profiles.
MAC_DefenderAV
MAC_FileVault
MAC_Firewall
Conclusion
In a world where cyber threats continue to proliferate, it is essential to fortify our macOS devices with robust security solutions. Microsoft Defender for macOS offers an invaluable defense against malware, viruses, and other malicious activities, providing an additional layer of protection to complement the built-in security features of macOS.
By following the comprehensive guide presented in this blog post, you can easily set up and configure Microsoft Defender for macOS, empowering yourself with a powerful and effective security solution. Leveraging Microsoft’s vast threat intelligence network and cutting-edge technologies, you can stay one step ahead of emerging threats and ensure the integrity and privacy of your digital assets.
The benefits of using Microsoft Defender for macOS extend beyond real-time threat detection and prevention. Its seamless integration with other Microsoft services and tools ensures a cohesive security ecosystem across your devices, allowing for centralized management and enhanced productivity. With features like cloud-based protection, automatic updates, and easy-to-use interface, Microsoft Defender offers a user-friendly experience without compromising on performance.
Furthermore, by choosing Microsoft Defender for macOS, you gain the advantage of a trusted and globally recognized brand. Microsoft’s long-standing commitment to security, privacy, and innovation ensures that you are backed by a company with an unwavering dedication to protecting its users.
Whether you are a home user, a small business owner, or part of a larger organization, the importance of cybersecurity cannot be overstated. By investing in a comprehensive solution like Microsoft Defender for macOS, you are proactively taking steps to safeguard your digital life and mitigate the risks associated with modern-day threats.
So, why wait? Take control of your macOS device’s security today and embark on a journey towards a safer digital environment. By implementing Microsoft Defender for macOS, you can rest easy knowing that your valuable data and personal information are shielded from malicious actors. Stay protected, stay vigilant, and embrace the power of Microsoft Defender for macOS.
Also have a look on the Microsoft Learn post on how to setup Defender for macOS: https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/mac-install-with-intune?view=o365-worldwide